Use Cases
External Vulnerability Scanner
Our external vulnerability scanner automates repetitive tasks to give you time for the creative work only you can do
Compliance standards such as the PCI DSS state that you must perform vulnerability scans four times a year with both an external and an internal vulnerability scanner.
External vulnerability scanning means you scan a target from outside the perimeter and without access to its network. It is the constant routine of security scans that leverages automation, attack surface mapping, scheduling, and sharing features for scale and accuracy.
Beyond compliance, external vulnerability scans bring many other benefits. They enable you to find and fix vulnerabilities that attackers could exploit. They should offer remediation guidance and help with patch management. They alert you to other potential weaknesses that could allow for a data breach, like open ports. And they help you identify outdated technologies in web servers, their operating system, and their impact on the network vulnerability posture.
Pentest-Tools.com is designed to ensure that you, your security team, and your enterprise harvest all these benefits and more! Here's what we can give you today.
Exceptional standard of information that covers everything you need to know
Laser focus on real-world demands, threats, and scenarios
Seamless integration with your wider, ongoing security processes
At a glance
How we outperform other external vulnerability scanners
Here are a few ways that Pentest-Tools.com gives you advanced external vulnerability scanning tools, features, and workflow gains. Our team also develops focused automation features designed to make the most of your security team’s resources and avoid accidental misconfigurations.
Comparison
Other external scanners
Pentest-Tools.com
Time and effort
Accuracy and realism
Automation and scale
Scanning and scheduling
Collaboration and integration
Optimize your workflow with high-value external scans
Pentest-Tools.com's comprehensive external vulnerability scanners help security specialists like you perform pentests that are information-rich, have a real-world basis, and are integrated into your ongoing security workflow.
The entire point of pentesting is to produce detailed information about security issues and system vulnerabilities, with factual proof to guide prioritization. You can use the Pentest-Tools.com platform for far-reaching external scans that deliver accurate results about your target’s attack surface, high-risk security issues, and remedial guidance.
Here’s how we ensure the quality and richness of that information for you.
External scan results that are rich in actionable information
Sniper Auto-Exploiter simulates external and authenticated attacks in a way that's both automatic and safe. Sniper scans provide rich results that include all its exploitation and post-exploitation steps, as well as the artefacts it has extracted. These results are displayed in both a console format and as a . The graph in particular provides a wealth of actionable findings represented as the visual summary of the target’s network configuration.
When you scan a web application with the Pentest-Tools.com Website Vulnerability Scanner, you receive rich findings you can automatically export into a detailed report that also includes key statistics. For example, the 'scan coverage information' feedback includes the number of URLs crawled, the total number of HTTP requests, the total number of HTTP request errors, and any unique injection points detected.
We have also enriched our editable DOCX pentest report format by adding an Appendix section that includes a list of the tools and techniques used during the test. This means you can quickly identify which tool was used on what target, at what start time.
External scans to evaluate and monitor your infrastructure
The Pentest-Tools.com Network Vulnerability Scanner is designed to assess the network perimeter and external security posture of your business. It works alongside three other integrated security testing tools. Findings from each of these feed into a single dashboard with multiple viewing and reporting options:
- Network Vulnerability Scan with OpenVAS assesses your network perimeter and infrastructure in depth
- SSL/TLS Vulnerability Scanner checks for SSL and TLS vulnerabilities and configuration issues
- DNS Server Scannerfinds name servers vulnerable to attacks that seek to reveal their zone files and all their confidential contents
Our enhanced Password Auditor extends your ability to discover potential access points and gain access to privileged information. That means you can identify weak or vulnerable credentials in web applications. But, more than this, you can automatically add detailed findings to your reports so you can export them with even richer recommendations.
We have many other tools that help build the attack surface automatically. You can find them under Reconnaissance Tools since it's their job to explore and map your network Attack Surface. Particularly important in this task are the Port Scanner with Nmap and the UDP Port Scanner.
Successful penetration testing tools exploit detected vulnerabilities using cyber attack methods that adversaries employ in real life. They allow you to see how your defenses perform if you suffer a malware attack in a real-world situation. You can close any gaps and harden security across your network or system before a real attack occurs.
External scan tests that are relevant and real
So how can a vulnerability scanning tool ensure that its test results stay realistic and technically accurate?
One way is to ensure that a security scanner tests for the most prolific and dangerous vulnerabilities. Pentest-Tools.com has a close relationship with OWASP (the Open Web Application Security Project), having contributed to the 2021 update of its famous Top 10. Every full web app scan searches for all old and new vulnerabilities from the OWASP Top 10. We also use other well-known security standards such as CWE (Common Weaknesses Enumeration) and CVE (Common Vulnerabilities and Exposures).
But, at Pentest-Tools.com, our commitment to accuracy goes deeper than this. It includes the ability to think like a malicious hacker, but act with the ethics of a white hat one.
The founder and CEO of Pentest-Tools.com is , who has over a decade's experience in ethical or 'white hat' hacking. Adrian has presented his findings at international security conferences like Hack.lu, DefCamp, Hacktivity, BlackHat Europe, and OWASP.
The Head of Professional Pentesting Services at Pentest-Tools.com, , also has senior ethical hacking experience which he uses every day to help customers from all over the world. We know how malicious hackers think and behave and we use their approach to show you what they go for first – and why!

External scanning that supports secure software development
External scans become more pressing as the technical stack of an organization grows over time. Regular penetration tests must be integrated into your SDLC (Software Development Life Cycle). They need to be quick, periodic, and specific. You have to know the instant they are completed and which essential findings they delivered. To maximize the time and expertize of your security team, scheduled scans are a must.
With Pentest-Tools.com’s integrated platform of security scanning tools and features, you can select:
- The scanning tool you require depending on your target (web apps, CMS, network)
- The type of scan you require (Light or Deep)
- When you need the scan to begin
- Your particular timezone
- How often you need the scan repeated (daily, weekly, monthly, quarterly)
- The frequency and recipients of notifications for scan activities, which you can get via email, webhooks, or to Slack channels

From the Automation tab of your Pentest-Tools.com dashboard, you can easily configure scheduled scans, pentest robots, and customizable scan templates. This is where you can manage and modify all the parameters of your scheduled scans. This saves you hours of manual work in setting up repetitive scans, collating results, and producing reports.
A comprehensive solution for scanning external assets
Shay Chen, CEO at Effective Security Ltd, acknowledges the benefits of Pentest-Tools.com for the external vulnerability scanning part of his work:
"Pentest-Tools.com is the Swiss army knife for anyone performing black-box external network security assessments and an all-in-one comprehensive toolset for external red team/asset mapping engagements. I used to rely on a wide range of tools when mapping and scanning external organization assets, but since I found this comprehensive solution, I rarely need to use more than one."
Start using the platform today
Unlock the full power and features of our platfom!
Compare pricing plans and discover more tools and features.
Can you conduct an external scan as an authenticated user?
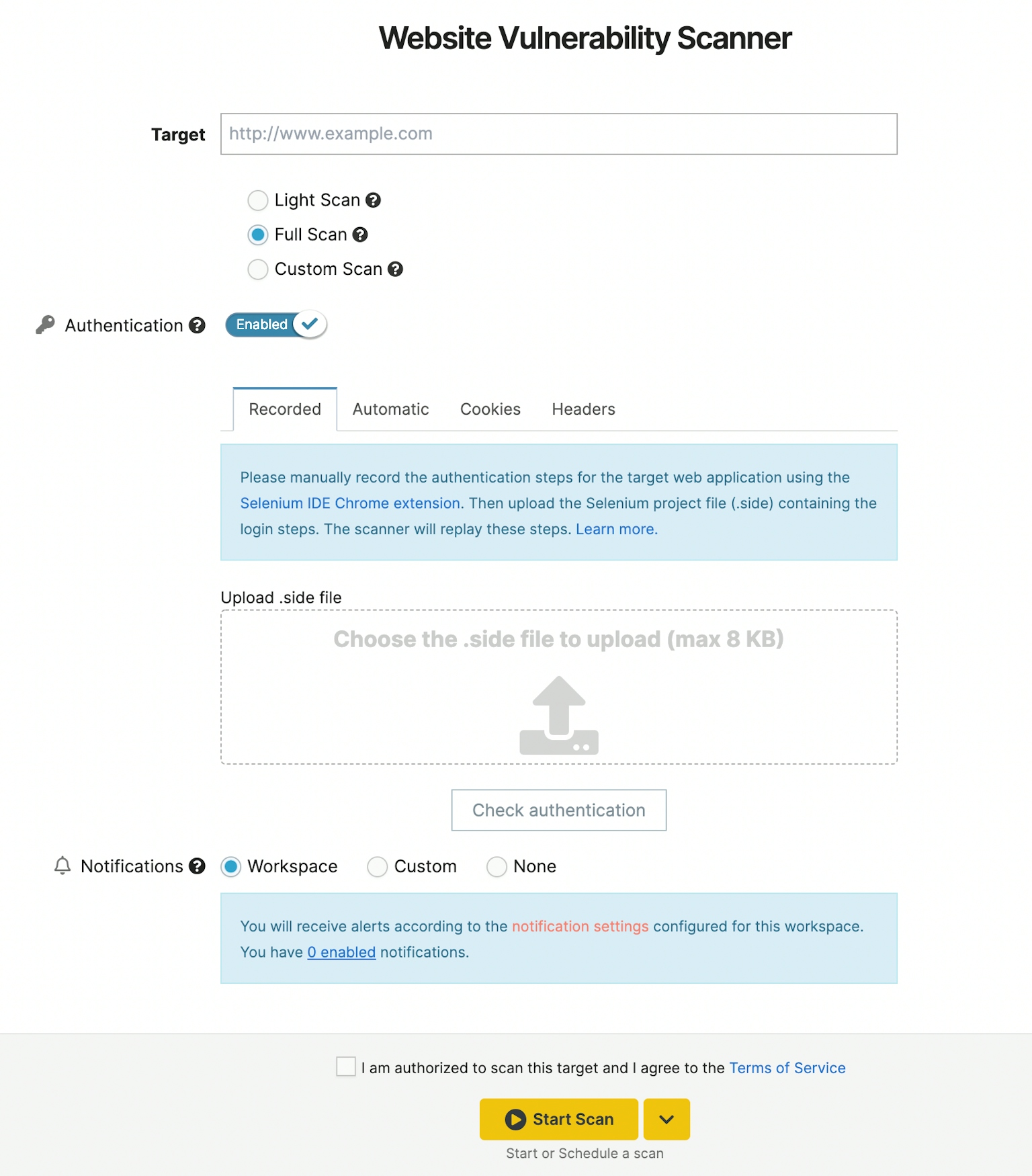
The Pentest-Tools.com vulnerability scanners enable authenticated scanning. This means you can scan targets as an authenticated user. You can perform in-depth scans and uncover critical vulnerabilities that an attacker could exploit after gaining access to your targets and data. The ability to is vital to the scanning process. You can choose one of four methods for performing authenticated web app vulnerability scans:
- Recording-based authentication – The Recorded method uses Selenium technology to record user events on the Pentest-Tools.com platform. In this way, you can use credentials to authenticate, then record this login sequence and upload this recording to the scanner, where it can be reused by others and in later scans.
- Automatic or Form-based authentication – This method allows you to run an authenticated scan by storing a valid set of credentials for the target application.
- Cookie-based authentication – This method allows you to run an authenticated scan using a valid cookie header from the target application.
- Headers authentication – This option allows you to run an authenticated scan by using valid headers from the target application.
Tools to use after running the WebsiteScanner
Reconnaissance Tools
Web Vulnerability Scanners
Network Vulnerability Scanners
Offensive Tools
Why security and IT pros are switching to Pentest-Tools.com for external vulnerability scanning
Peter Bassil from Hedgehog Security had this to say about his confidence in Pentest-Tools.com’s capabilities to scan for external vulnerabilities:
- Helps produce "confidence around the vulnerability" found in terms of its real "exploitability"
- Gives teams "a more solid jumping off point" to find how a malicious hacker might take the vulnerability and "exploit it in the real world"
- Works by the principle that "the more information you can have on a vulnerability, the better"
- Sniper Automatic Exploiter helps "to massively enrich the data that's being presented and it's going to make the Pentest-Tools.com tool framework significantly more valuable to people"
"So the team can literally run the scans, pull it [the data] into our reporting engine and just browse through it and see what exploits we know about already. It just makes a lot less work for them. It means I can get to the fun stuff quicker."
Easy, quick, and intuitive to use
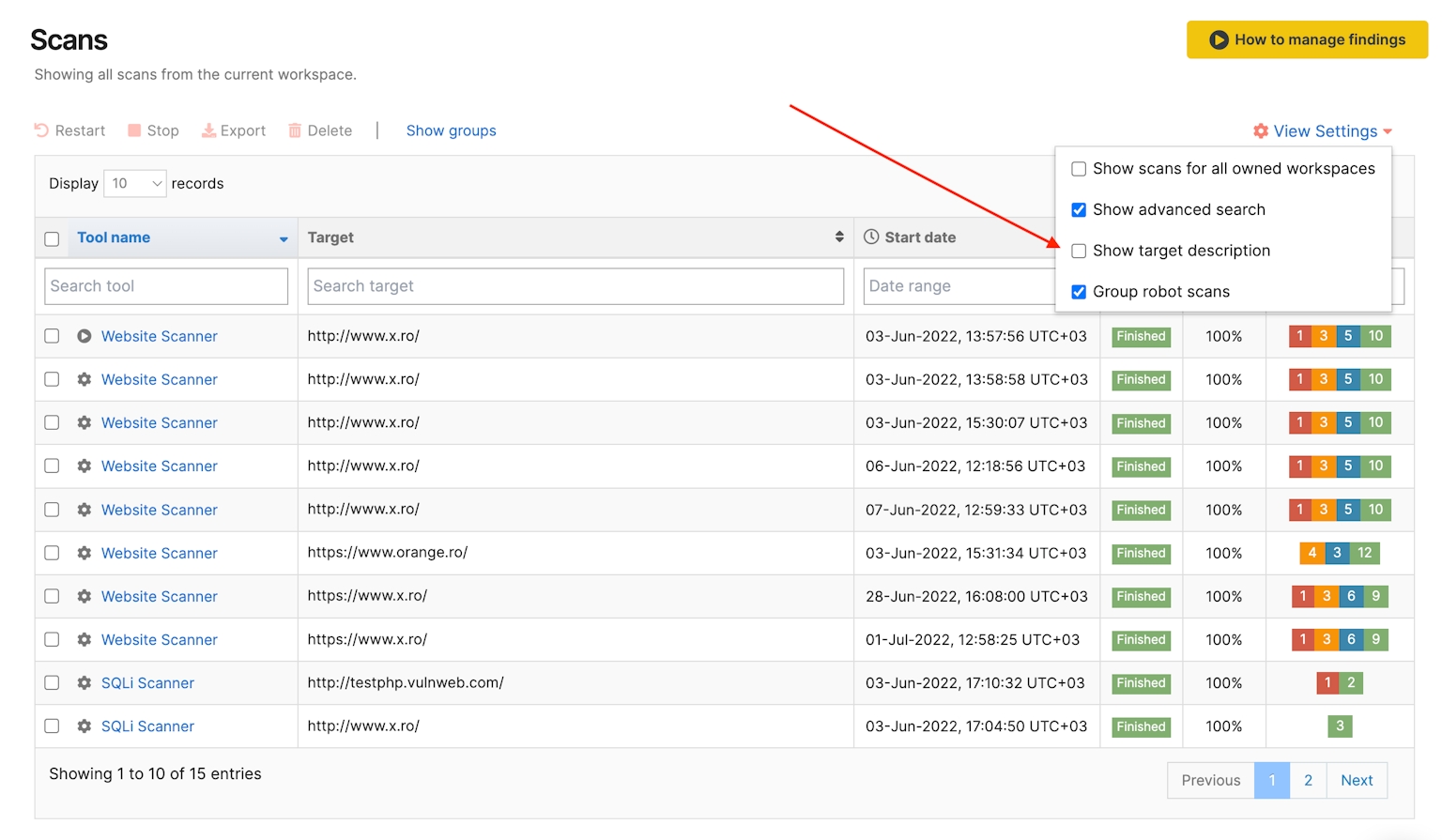
The Pentest-Tools.com team prioritized user experience from the earliest iterations of our platform design. This is why the Pentest-Tools.com UI has evolved to enhance your experience of using our professional set of tools. A fluid UI eliminates distractions and makes navigation an intuitive journey. You can easily employ filters and export options in Findings to view the results you want. And, to make information easy to digest, there are features like the .
Although it may not be your go-to use case, our designers have ensured that the mobile version is as easy and quick to use as the desktop.
One example of this is the addition of an option on the dashboard interface that allows you to easily view the target description for all your scans, including scheduled ones. We’ve also streamlined many smaller tasks, meaning less configuration on your part.
For instance, you can add specific findings to reports, delete headers you no longer need, or share items and workspaces across your team, all with preset options.
Testing for the most common vulnerabilities and critical threats
There are many cybersecurity organizations, like NIST and CISA, that publish lists of the most critical risks facing organizations. From the start, we’ve referenced the most well-known and authoritative of these lists and made them an integral part of our scanning technology.
For example, the OWASP Top 10 list is an open-source industry standard that is known and used as a global reference for risk minimization and security by design.
Pentest-Tools.com’s pre-built pentest robots are designed to automatically detect and identify OWASP Top 10 vulnerabilities (and more). Our reports’ findings include OWASP 2017/2021 detected security risks along with their CWE reference. After each scan, you can view more details on an OWASP risk from the Findings list, visualize it from the Scans window, and automatically share these details with the reports.
The current version of the Pentest-Tools.com platform is a custom engine built in-house by our team of security specialists. Our pentesting flows and assessment workflows integrate the principles and tactics from industry staples such as the OWASP Web Security Testing Guide. And, since 2021, we’ve become a Corporate member of OWASP, contributing our expertise and data freely to improve the software security landscape around the world.
Minimizing and even eliminating false positives
In both network vulnerability scans and external web vulnerability assessments , it isn't enough just to pinpoint vulnerabilities. You must validate each one as a real security hole and direct threat to your organization’s digital collateral and data. This means you must be aware of the problem of false positives.
The Pentest-Tools.com scanners offer an option of Light or Deep scan. While the Light scan is faster, our Support documentation makes it clear that it is prone to returning false positives because it relies on the version reported by the services, which may be inaccurate.
However, from the Pentest-Tools.com vulnerability management feature – found in the Findings section of the dashboard – you can verify findings, change their risk level, mark them as fixed or ignored, and generate reports from which you can exclude unverified findings.
Our Website Vulnerability Scannerautomatically validates findings and tags them as Confirmed so you can select and add them to your report. And our Network Vulnerability Scanner uses Sniper Auto-Exploiter modules to give you solid proof for vulnerability validation.
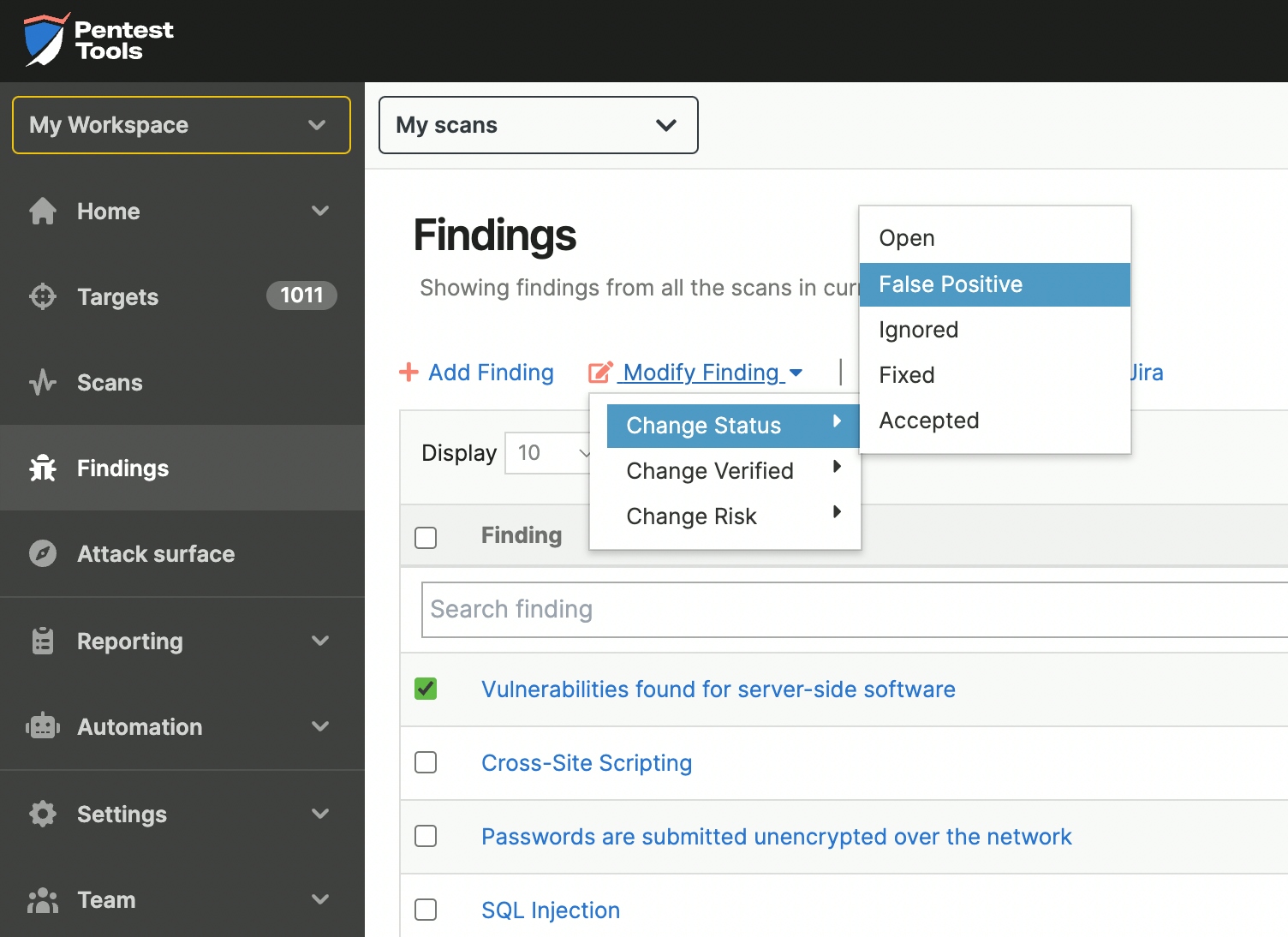
If a finding is unconfirmed, you must conduct a manual check to see if it’s a false positive or not – and mark it accordingly. Pentest-Tools.com can help you with this in two ways. You can conduct a check yourself using our support article How to validate findings? Or, as managed pentesting service providers, our security specialists can validate each finding manually in every engagement, leaving you with zero false positives.
An external scan report that’s easy to digest and apply
Reporting is an often neglected feature of the external scanning process, with all the attention and effort focused instead on the scanning tools. But the report is often all that a manager or customer cares about or sees.
After all your work, can they even understand what they're reading? And will they know what they're supposed to do with all that information?
For report readers, Pentest-Tools.com advanced, editable reports feature:
- A categorized breakdown of all types of discovered weaknesses and threats
- A visual representation of the findings with their criticality levels
- A customizable table with the more significant findings, their risk level, and their verified status
- Detailed and actionable recommendations for each vulnerability, to help you prioritize the most important business assets
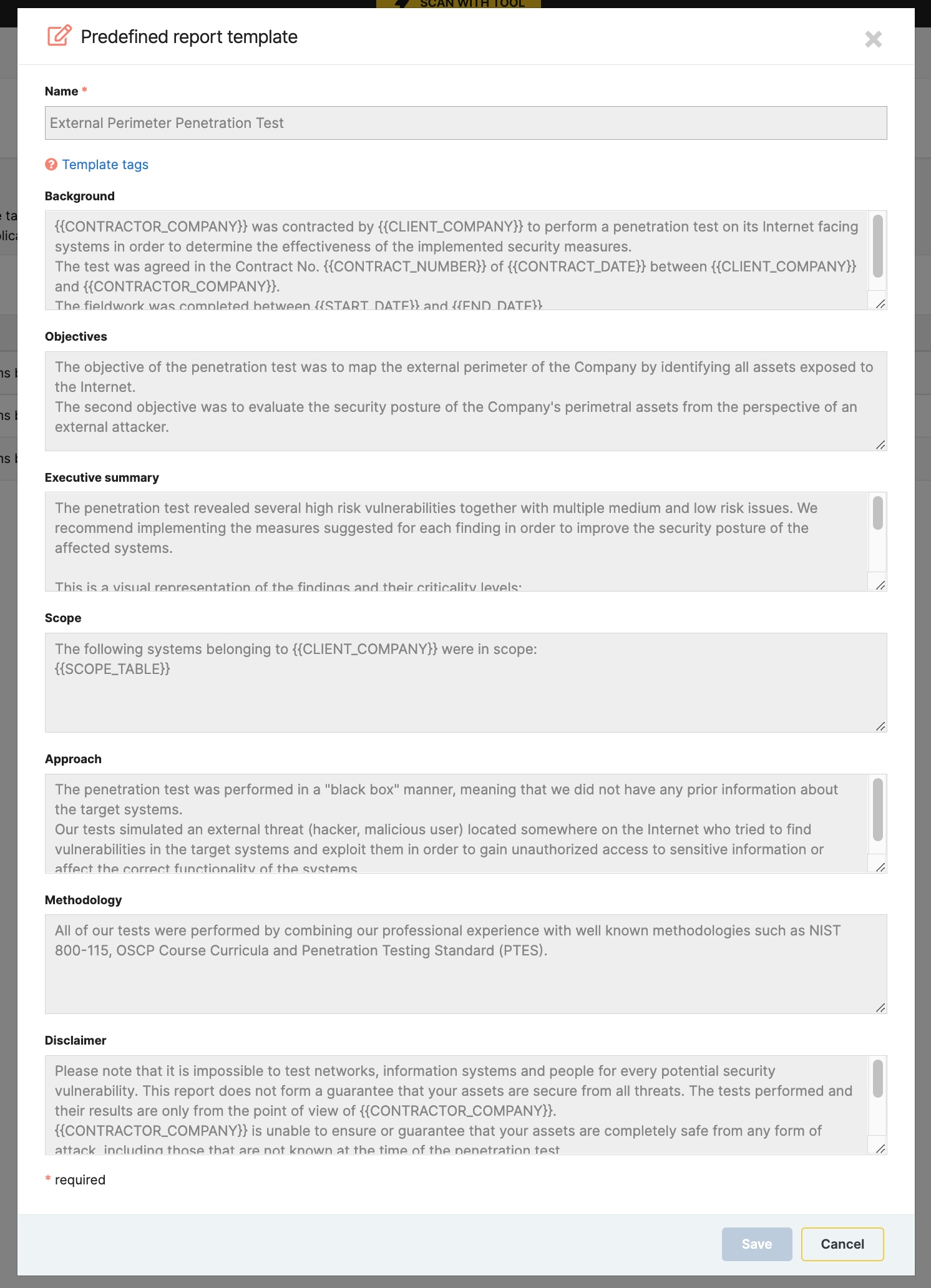
- Multiple sections that break down the report material into easily digestible and fully customizable chunks, such as Background, Methodology, Executive Summary, and Findings & Remediation
- Editable DOCX reports that you can easily customize, including with your own logo
A pentest report tool that takes the pain away
As for report writers, structuring, compiling, and writing pentest reports is often a tedious, time-consuming part of the work. We understand this taxing task and have developed an advanced reporting tool that constantly collates your scan results, showcases your efforts, and presents a streamlined reading experience.
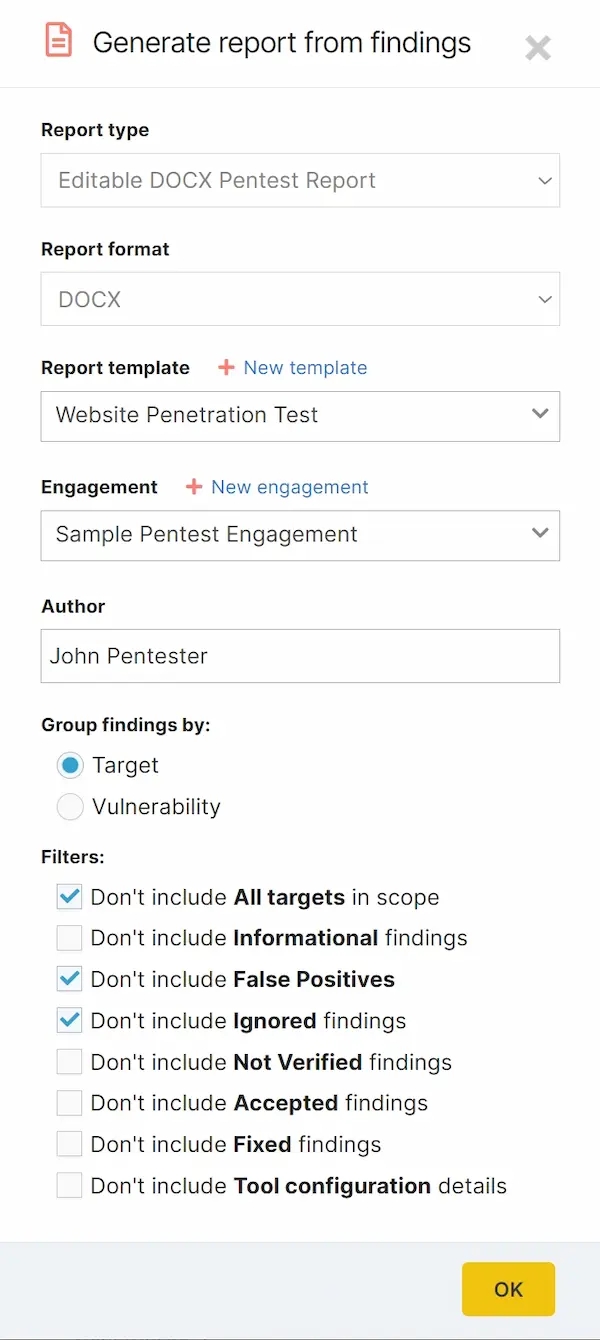
Reports come with pre-filled data and allow you to:
- Choose from multiple predefined pentest report templates – or you can create your own
- Select relevant findings – by target or vulnerability – with handy filters
- Exclude unverified findings, false positives, informational findings, or any other findings that are irrelevant
- Make reports more comprehensive by adding manual findings from other sources
- Create reusable Findings templates for future engagements
Common Questions
External vulnerability scanning FAQs
The Light scan is passive, partial and generates 20 HTTP requests (max) to the server. The Deep scan is aggressive, comprehensive, and sends 10,000 HTTP requests (max) to the server, and can take several hours to complete. It includes all the Light scan tests but adds some complex tests. There are also more risks in performing a deep website scan.