CVE-2023-44487 Scanner HTTP/2 Rapid Reset Vulnerability
This free CVE-2023-44487 Scanner checks if your target is vulnerable to CVE-2023-44487 – aka the Rapid Reset vulnerability. Unauthenticated attackers can exploit this high-risk security issue to cause a Denial of Service attack.
This CVE-2023-44487 Scanner checks if the target supports the HTTP/2 protocol and the HTTP/2 RST_STREAM directive.
If you’d like to scan other custom ports, this free tool is part of the premium version of our Network Vulnerability Scanner, which detects over 11.000 CVEs using its Deep Scan feature. For full access to it and other 20+ tools, check out our pricing plans.
This free CVE-2023-44487 Scanner checks if your target is vulnerable to CVE-2023-44487 – aka the Rapid Reset vulnerability. Unauthenticated attackers can exploit this high-risk security issue to cause a Denial of Service attack.
This CVE-2023-44487 Scanner checks if the target supports the HTTP/2 protocol and the HTTP/2 RST_STREAM directive.
CVE-2023-44487 (HTTP/2 Rapid Reset Vulnerability) technical details
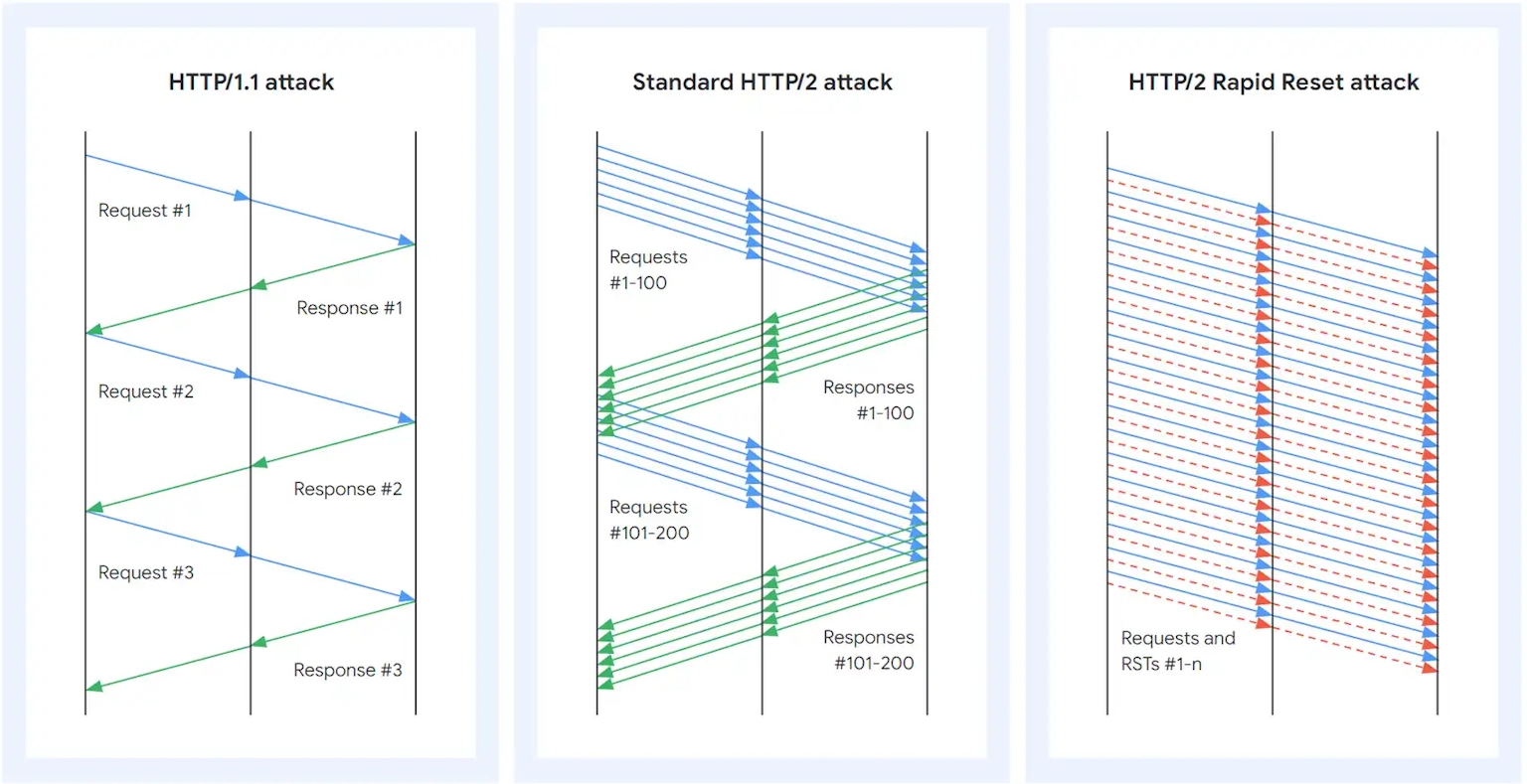
The HTTP/2 network protocol has a Denial of Service (DoS) vulnerability, identified as CVE-2023-44487, which attackers can exploit to cause a service outage.
This issue comes from processing HTTP/2 requests incorrectly, which enables an unauthenticated remote attacker to trigger a DoS attack by manipulating these requests.
CVE-2023-44487 severity
CVE-2023-44487 has a high severity CVSSv3 score of 7.5 and it is included in CISA’s Known Exploited Vulnerabilities .
CVE-2023-44487 mitigation
If you’re looking for information on how to fix CVE-2023-44487, here are the main guidelines for the main types of technologies impacted.
As a general CVE-2023-44487 remediation, it’s recommended to use the settings provided by the vendor of the server where your HTTP/2 network protocol is running.
CVE-2023-44487 NGINX mitigation
For NGINX, it is recommended to:
- Update NGINX to the latest version that has addressed this vulnerability. As vulnerabilities like CVE-2023-44487 are typically patched swiftly, ensure your system is running an updated version that includes the security fix.
- Make specific configuration adjustments to limit the impact of potential HTTP/2 exploitation, if updating NGINX is not viable:
Disable HTTP/2: If HTTP/2 is not a requirement for your environment, you can disable it temporarily until you can apply the necessary updates. Modify the NGINX configuration by removing or commenting out any http2 parameters in your server block settings.
listen 443 ssl; # Remove 'http2' from this line if presentLimiting Connection and Stream Parameters: Configure limits for the number of concurrent streams and connections per session to reduce the risk of resource exhaustion:
http2_max_concurrent_streams 64; # Limit the number of concurrent streams
http2_max_requests 1000; # Limit the number of requests per connectionCVE-2023-44487 Apache mitigation
For Apache, it is recommended to:
- Update your Apache HTTP server to the latest version. Apache has released patches for this vulnerability in versions 2.4.56 and later. Ensure you are running an updated version that includes these security patches.
- Check your Apache configuration, if you cannot immediately update your server or as an additional layer of security. Focus on settings related to the
mod_proxymodule, especially how it handles request headers and data forwarding. Ensure themod_proxyis correctly configured to handle unexpected or malformed headers. You can also temporarily disable features that aren't necessary for your operations.
About our Network Vulnerability Scanner
Our Network Vulnerability Scanner is a well-rounded tool for all your network security assessments.
It combines multiple engines and fine-tuned (customizable) scan settings which surface over 20.000 critical vulnerabilities, misconfigurations, and outdated services.
Each scan automatically updates your attack surface and provides an up-to-date map for planning targeted attacks or strategic lateral movements.
Explore a sample report which includes a vulnerability summary, automatically confirmed findings, evidence, and more.
See what else it can doFAQs
What is HTTP/2?
HTTP/2 is the second major version of the Hypertext Transfer Protocol, used primarily for transmitting data on the internet.
It was developed by the IETF (Internet Engineering Task Force) and formalized as a standard in May 2015 with the publication of RFC 7540.
HTTP/2 was designed to improve the efficiency and speed of data transfer over the network compared to its predecessor, HTTP/1.1.
How widespread is the use of the HTTP/2 protocol?
According to a W3Techs report, over one-third (35%) of websites globally are using HTTP/2.
What is the potential impact of CVE-2023-44487?
Exploiting CVE-2023-44487 allows an unauthenticated remote attacker to cause a Denial of Service attack. This type of cyberattack can have severe consequences for an organization, affecting multiple aspects of their operations and finances:
- Disrupt operations: because a DoS attack typically floods a network or system with excessive traffic, it can render it unavailable to legitimate users. This can halt operations, affect production, lead to a decrease in sales, make it difficult to provide customer service, and impact other critical business functions. For businesses that rely heavily on online transactions or services, such as e-commerce sites or financial services, the impact can be particularly severe.
- Financial loss: operational disruptions lead to immediate financial loss because organizations can no longer acquire new customers or serve their existing ones. Additionally, businesses may have to shoulder the costs of mitigating the attack, from hiring cybersecurity experts to purchasing additional hardware or software, or increasing bandwidth. There can also be legal and regulatory fines if the disruption breaches compliance requirements.