Subdomain Takeover
Technical details
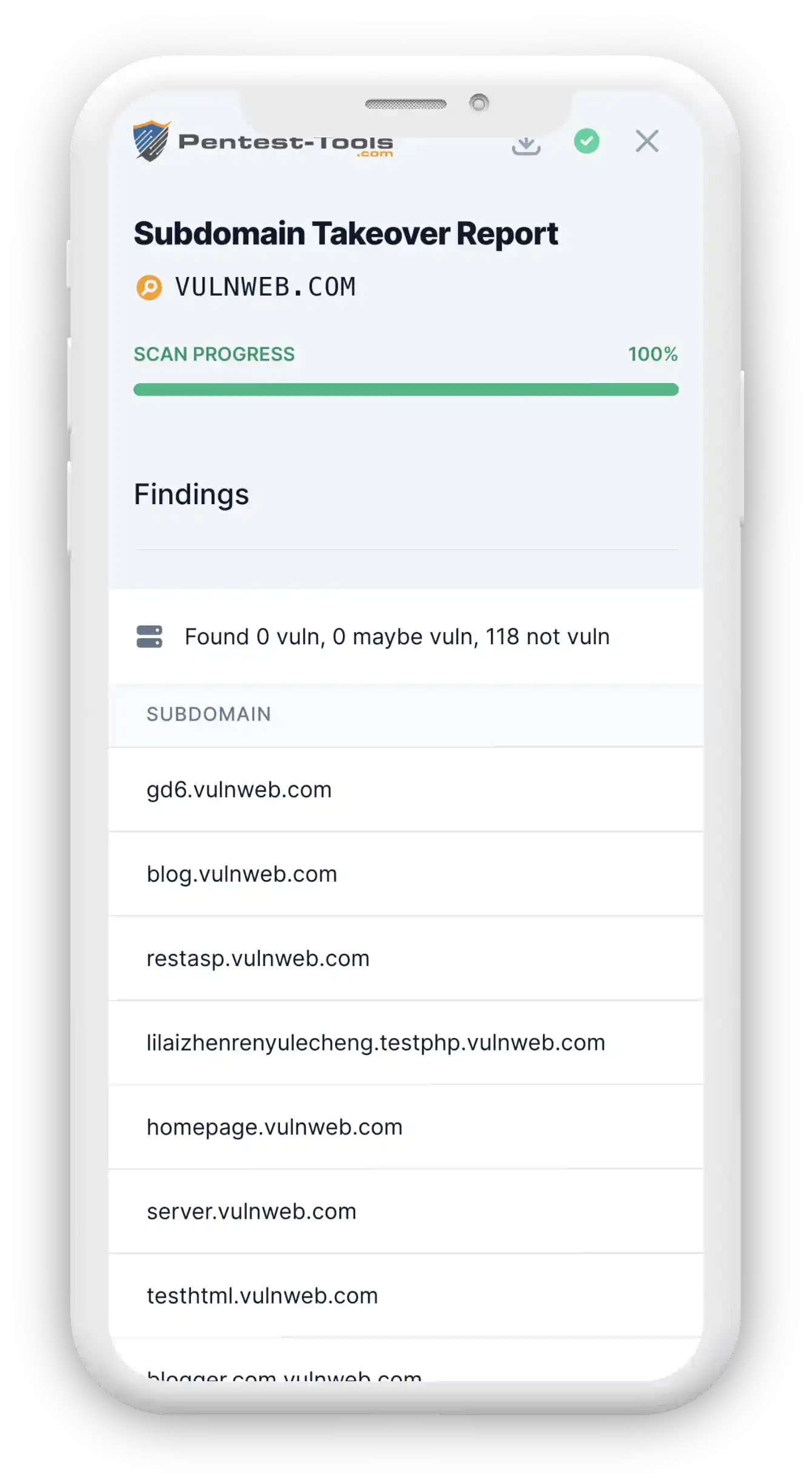
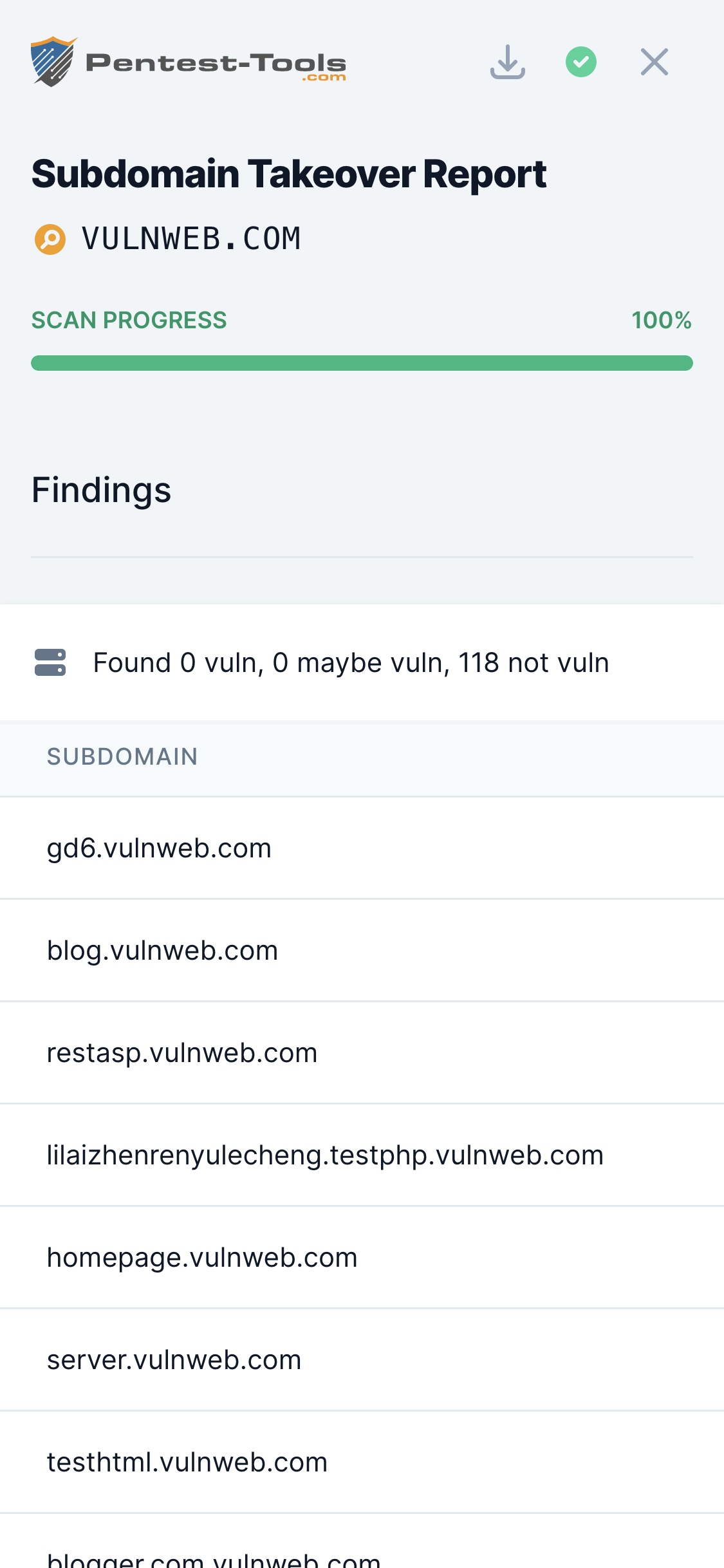
Subdomain Takeover is a type of vulnerability that appears when an organization has configured a DNS CNAME entry for one of its subdomains pointing to an external service (e.g. Heroku, Github, Bitbucket, Desk, Squarespace, Shopify, etc.) but no longer uses that service. This enables an attacker to register to the external service and claim the affected subdomain.
As a result, the attacker could host malicious code (e.g. for stealing HTTP cookies) on the organization's subdomain and use it to attack legitimate users.
Parameters
| Parameter | Description |
|---|---|
| Target domain | This is a domain name (e.g. yahoo.com) whose subdomains vulnerable to takeover the tool will search for. |
How it works
The tool uses all the techniques from Subdomain Finder to identify existing subdomains for the target domain. It then searches for CNAME DNS entries pointing to external services and it tries to visit the web pages at those locations. If the pages contain some specific keywords (depending on the external service), the subdomain is declared vulnerable.