Web Application Firewall Detector
Find out which WAF your target is using and how effective it is. Our WAF detection tool triggers and detects the web application firewall – and then tries to bypass it by finding the Origin IP.
Get actionable recon information for manual investigation and customizing payloads. Whenever it can, our WAF Detector gives you the IP of the origin server behind the firewall so you can send requests directly to it.
Paid plans give you access to its full capabilities, plus other 20+ security testing tools and features.
Unlock full capabilities
There's so much you can do with this tool!
Plus, access to it means full access to all 20+ tools on the platform.
Find out which WAF your target is using and how effective it is. Our WAF detection tool triggers and detects the web application firewall – and then tries to bypass it by finding the Origin IP.
Get actionable recon information for manual investigation and customizing payloads. Whenever it can, our WAF Detector gives you the IP of the origin server behind the firewall so you can send requests directly to it.
Paid plans give you access to its full capabilities, plus other 20+ security testing tools and features.
Reporting
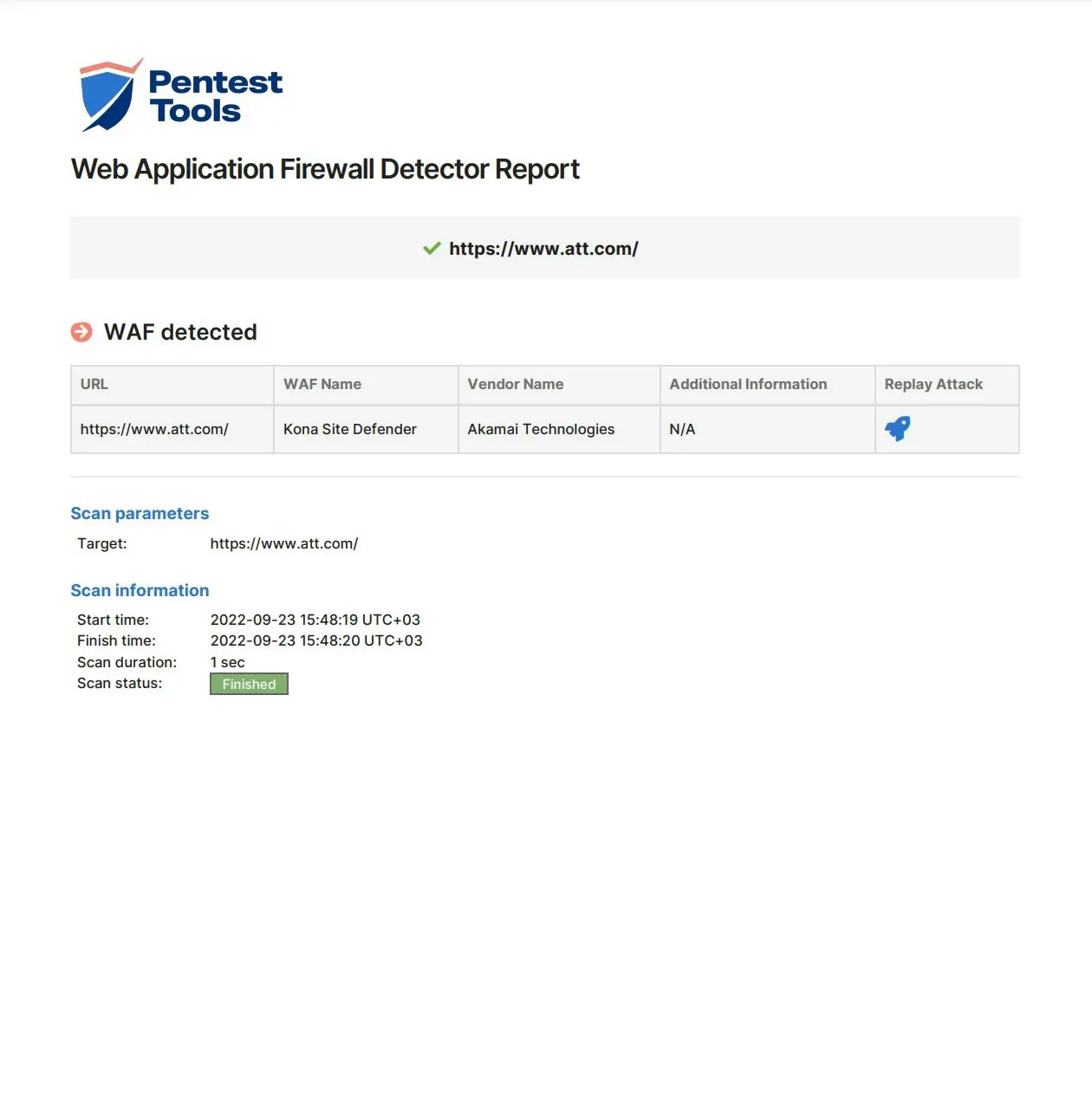
Sample Web Application Firewall Detector report
Each scan with our web based WAF Detector generates detailed results which are easy to export in PDF, HTML, CSV, JSON, or XLSX reports. Each report includes:
WAF name and vendor
Replay attack
Origin IP
Better vulnerability discovery.Faster pentest reporting.
Get instant access to custom vulnerability scanners and automation features that simplify the pentesting process and produce valuable results. The platform helps you cover all the stages of an engagement, from information gathering to website scanning, network scanning, exploitation and reporting.
Scanning capabilities
How our Web Application Firewall Detector works
- 1
Non-harmful attack simulation
To detect the web application firewall behind your target, our tool simulates common web attacks against the web app (i.e. XSS, SQLi, Local File Inclusion, OS Command Injection). For each simulated attack, it tries to match the HTTP response to a known WAF using both open-source and custom WAF signatures.
- 2
Origin IP reconnaissance and port scanning
Our WAF Detector tool actively tries to discover the origin IP behind a web application firewall. It first collects candidate origin IP addresses based on historical IP addresses the target hostname resolved to. It then probes these IPs with small port scans (ports 80, 443, 8080, and 8443) that focus on HTTP servers . Comparing the responses from these servers to a normal (i.e. non-firewall) response, the WAF detection tool zeroes in on the ones with the highest similarity. Finally, by re-simulating an attack, the detector identifies the IP with the most similar response that doesn't trigger the WAF.
- 3
Built-in option for reducing scan errors
If your target has multiple redirects, enabling the Follow redirects option can help you automatically avoid scanning errors.
Use cases
What you can do with the Web Application Firewall Detector
Craft more powerful payloads
Assess the target independent of its WAF
Make sure the web app and WAF are configured correctly
Or check out 20+ more included tools
We built the Web Application Firewall Detector for
FAQ
Common questions about the Web Application Firewall Detector
Yes, you can use the WAF Detector through the Pentest-Tools.com API.