SQLi Exploiter
Technical details
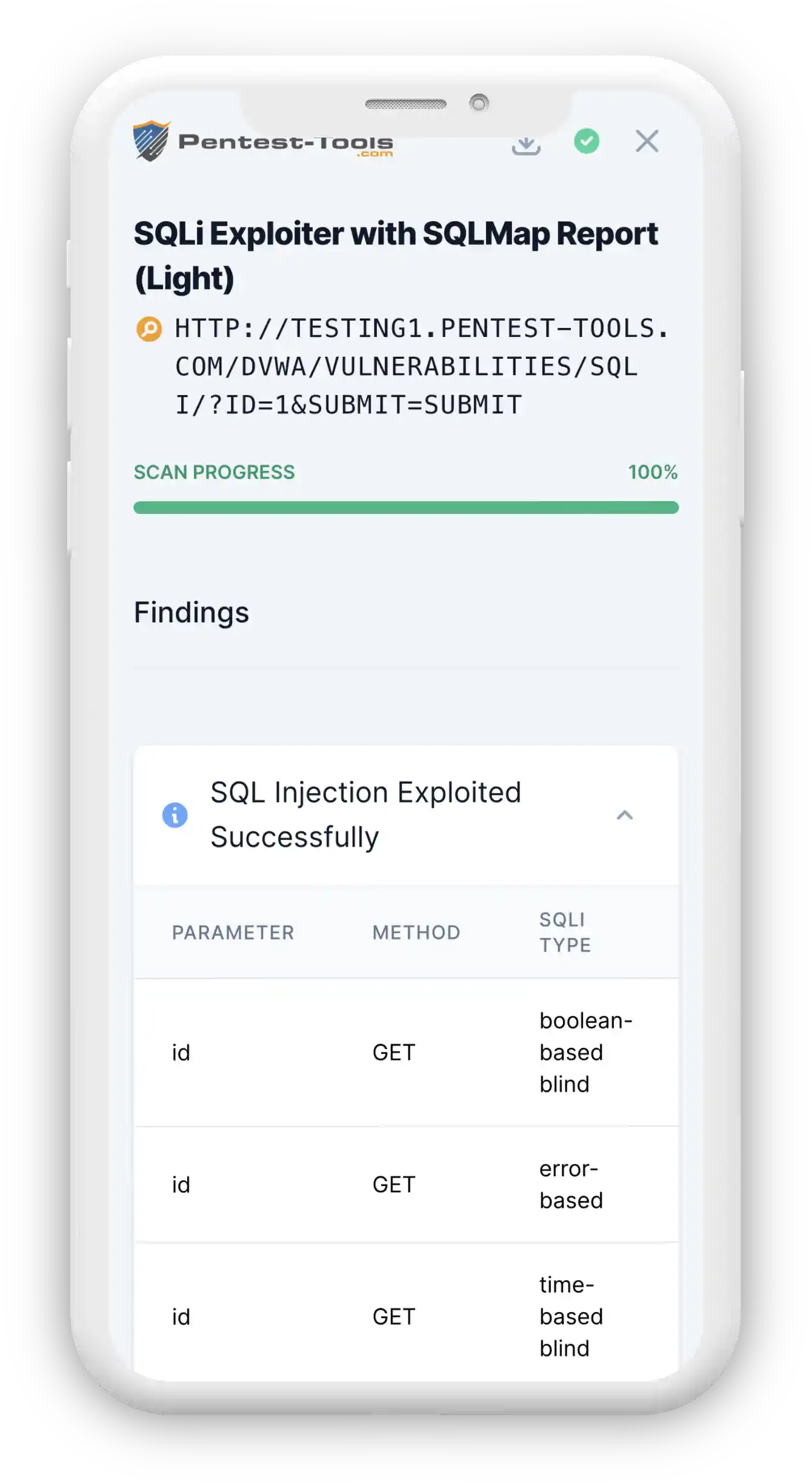
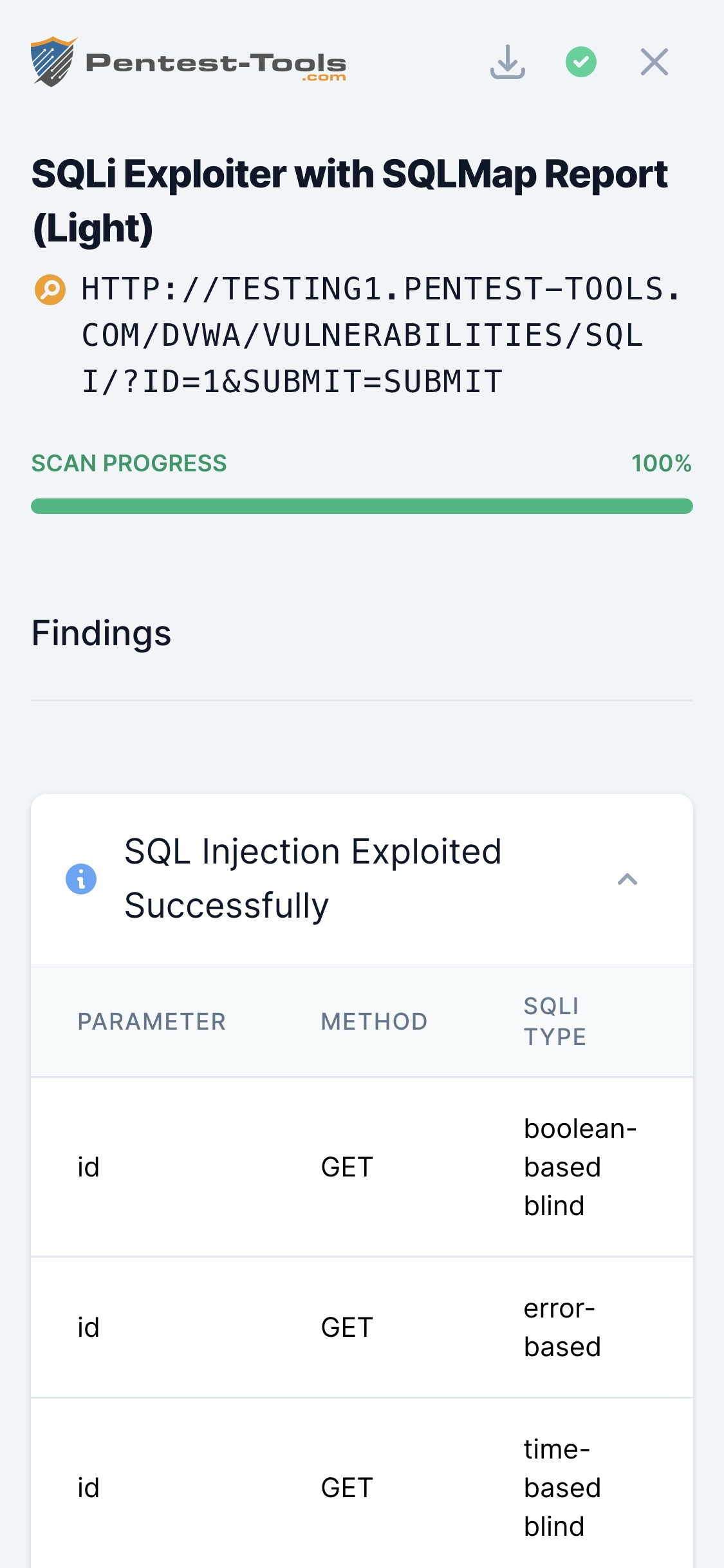
The tool uses SQLMap to test a variety of payloads against the target to determine which parameters are vulnerable. Once the tool finds and tests all the parameters and discovers that at least one of them was confirmed as vulnerable, it will use it to extract the specified information from the database.
Warning
Parameters
| Parameter | Description |
|---|---|
| Target URL | This is the URL of the website that will be scanned. All URLs must start with http or https. |
| Method | Choose the HTTP method that will be used to send the requests. Choosing POST will also ask you for the POST Data you want to include in the payload. |
| POST Data | A string containing the data that will be sent through POST (e.g. id=1). |
| Enumeration | Choose which data you would like to extract from the database. |
| Light Crawling | Crawl the website up to second-level links and try to discover SQLi vulnerabilities automatically. |
| Advanced | Toggle advanced options. |
| Cookie header | HTTP Cookie header to include in each request. Useful when you want to conduct tests on a page after login (e.g.: "PHPSESSID=a8fh54s.."). |
| Test parameters | A comma-separated list of parameters to be tested. If empty, SQLMap will try to determine the available parameters by itself. |
| Database type | Force SQLMap to only test payloads for this specific database. If none is specified, the tool will detect the database type by itself. |
| Prefix | String to prepend to each payload |
| Suffix | String to append to each payload |
| Tamper | Use the specified script to tamper (modify) payloads. |
| Level | The diversity of the tests performed. By default, SQLMap will test all GET and POST parameters specified / found. However, you can add additional entry points using the level option. For example, Level 2 adds HTTP Cookie testing, while Level 3 adds User Agent / Referer testing. The higher the level, the longer the scan takes. |
| Risk | How aggressive the tests should be. If you choose a higher risk, SQLMap will include more resource-intensive tests, which might make the database temporarily inaccessible to legitimate users (for the duration of the test). For example, Risk 2 will run heavy time-based SQL Injection queries alongside the default Risk 1 payloads. Also, the higher the risk, the longer the scan takes. |
| HTTP Code | HTTP code to match when a query is evaluated to true |
| Techniques | Choose which type of SQLi techniques to use. Default: all (BEUSTQ). |
How it works
The tool is a web interface for the well-known SQLMap, which is executed with the proper parameters to provide speed and accuracy.
It tests a variety of payloads against the target to determine which parameters are vulnerable. Once SQLi Exploiter finds and tests all the parameters and discovers that at least one of them was confirmed as vulnerable, it will use it to extract the specified information from the database.
Detailed information about SQL Injection, including solutions on how to remediate this vulnerability, can be found in the OWASP SQL Injection Page.