Sample Network Vulnerability Scanner report
Explore a real-life network assessment report. Browse through key sections, examine risk rating graphs, and review in-depth technical findings to get an accurate preview of the report's structure and content.
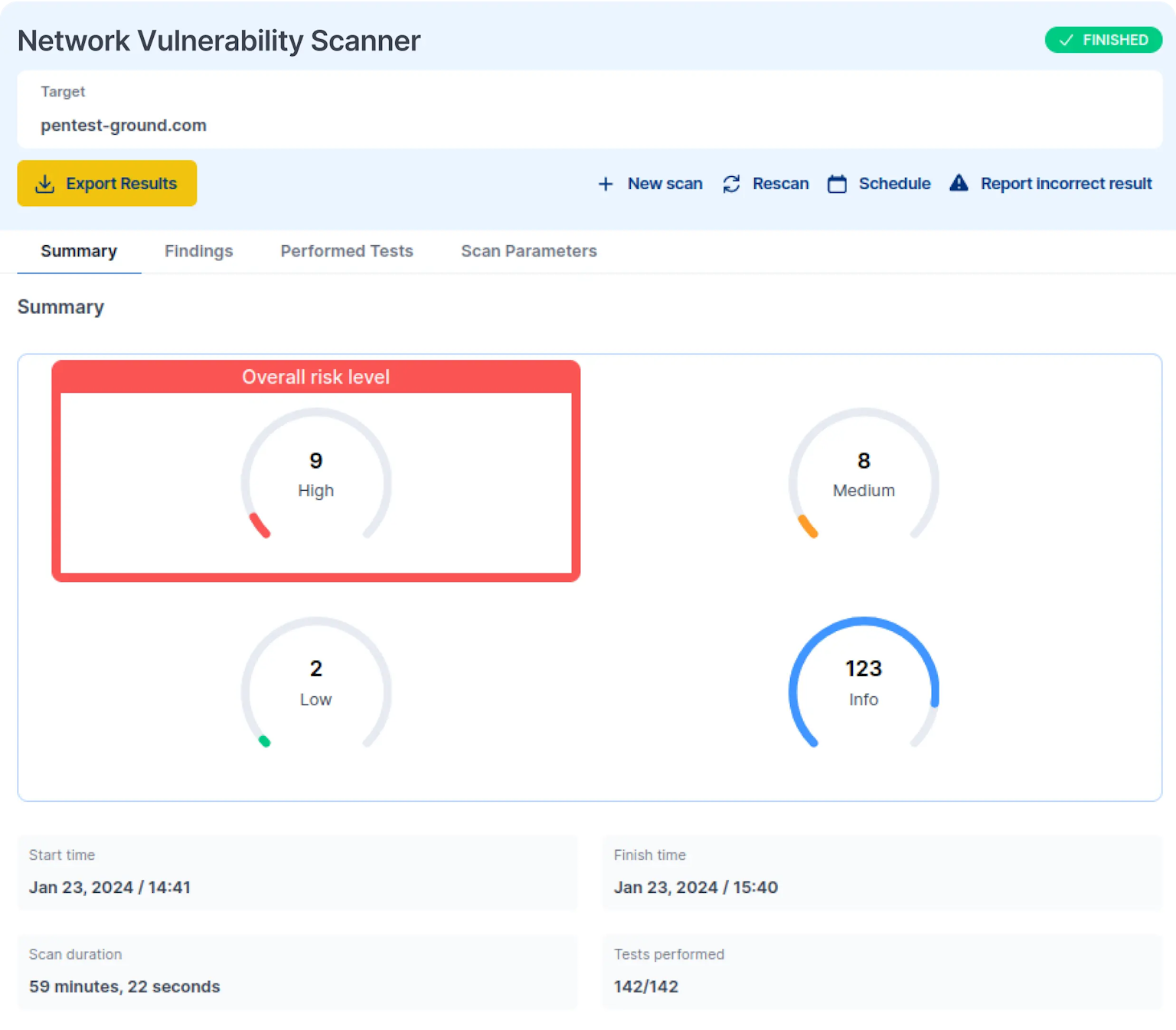
Provides a quick and complete look at the included security issues, showing their potential impact and urgency. This helps prioritize and address critical vulnerabilities.
How does the Network Vulnerability Scanner work?
The Network Vulnerability Scanner confirms if the target host is alive, pinpoints open ports and associated services, then runs the vulnerability detection routines.
Featuring four complementary scanning engines, it checks software versions against a regularly updated CVE database, uses OpenVAS to target network services, runs custom Sniper modules for critical vulnerability detection, and automates network security checks through Nuclei templates.
Want more details? Check out the full technical documentation.
It's really easy to scan your network for vulnerabilities
No setup required. No processing power limits
Operating as a cloud-based scanner, the Network Vulnerability Scanner works out of the box. No need to install anything on your end to scan public-facing or internal network hosts.
Scheduling & running parallel scans
Automatically execute recurring and routine scans for your network hosts. Combine scheduling with the option to run multiple scans in parallel for a productivity boost, and get notifications for specific findings.
API access for easy integration
Initiate scans programmatically with our REST API. Integrate findings into your internal processes - CI/CD workflows, data sources, or custom applications - for an efficient and automated way to use our Network Scanner.
Internal scanning
Detect vulnerabilities, misconfigurations, and other security issues in hosts from internal networks, intranets, private clouds, or restricted-access systems. Quick and easy to set up, our VPN agent directs traffic from our servers to your target’s internal network.
Integrations
The Network Vulnerability Scanner integrates seamlessly with your preferred office and productivity tools: Jira, Slack, email, and Webhooks. Simplify your and your team’s workflow with notifications for scan results for findings truly worth your time.
Customer reviews
Pentest-Tools.com allows for rapid deployment and automation of many industry-standard security tools, then organizes the results into an easy-to-view 'attack surface'. This allows our penetration testers more time to focus on vulnerability analysis and exploitation.
An added benefit that has been fantastic is that the ease of use allows new employees to add value to an engagement on their first day.
Travis DeForge
Security Engineering Manager at Gotham Security
United States of America 🇺🇸

Common questions about network vulnerability scanning
Check out our quick setup guide to quickly familiarize yourself with the tool and launch your network scan. We designed it to help you make the most of Pentest-Tools.com effortlessly.
Get your network vulnerability assessment rolling in just a few easy steps!

