Network Vulnerability Scanner
Overview
Within a company's infrastructure, the network perimeter acts as a protective barrier, segregating the internal network from external entities. Nevertheless, certain company resources, such as the website, need to be accessible from the outside. Consequently, network services like FTP, DNS, HTTP, among others, become exposed beyond the network perimeter to grant this access.
To address the inherent security risks associated with exposed services, a Network Vulnerability Scanner systematically probes the network perimeter, mapping all its services and evaluating whether they have any exploitable vulnerabilities.
The Network Vulnerability Scanner on Pentest-Tools.com is designed to identify and assess weak configurations, vulnerabilities, and other security flaws within a computer network. Its primary purpose is to proactively detect potential entry points or weaknesses that attackers could exploit to gain unauthorized access, compromise, or disrupt the network.
The Network Vulnerability Scanner operates in two successive steps:
Discovery: The Network Vulnerability Scanner determines if the host is alive and then it runs a port scan to determine the open ports and the associated services running on those ports.
Vulnerability assessment: The Network Vulnerability Scanner performs vulnerability scanning by checking for known security flaws in software versions, configurations, or system settings. It accomplishes this by using four distinct scanning engines that can be used independently or in combination, depending on the selected scan type:
The Version-based scan engine compares the services and software versions with a CVE database; this database gets regular updates with information about new security vulnerabilities, exploits, and patches.
The OpenVAS scan engine is an advanced, open-source vulnerability scanner capable of actively identifying numerous vulnerabilities across network services. Its comprehensive scanning capabilities extend to services running on multiple protocols such as SMTP, DNS, SSH, RDP, VNC, HTTP, and various others.
The Sniper scan engine consists of a set of custom vulnerability checks developed internally by our team. These checks are named Sniper modules, and they provide quick detection of critical vulnerabilities in high-profile software.
The Nuclei scan engine automates the detection of security vulnerabilities in web applications and network services by leveraging its own framework for writing and executing security checks (Nuclei templates).
By using a network vulnerability scanner, security and IT specialists can proactively identify and address security weaknesses, reducing the risk of unauthorized access, data breaches, and system compromises. It enables security teams to stay informed about the network's security posture and take necessary measures to protect the network and its assets from potential threats.
Usage
Security professionals use the Network Vulnerability Scanner to actively detect a wide range of security issues and misconfigurations in network services, operating systems, and web servers. It can help you with:
→ Infrastructure penetration testing
The Network Vulnerability Scanner provides you with a comprehensive overview of the easily exploitable vulnerabilities in your engagement, allowing you to focus on more advanced tests. Since it works online and comes with a preconfigured setup, the tool ensures effortless usability, saving you valuable time and effort.
→ Internal network scanning
Test internal networks as if you were on-premises without time-consuming scripts and configurations. This pentesting tool allows you to scan internal networks through a ready-to-use VPN and start your work in minutes.
→ Scanning for critical common vulnerabilities and exposures
Find high-risk vulnerabilities such as Log4Shell, ProxyShell, ProxyLogon, and many others. Our security researchers integrate detection for widespread CVEs under active attack as rapidly as possible. We keep adding custom modules that cover vulnerabilities both in the MITRE CVE program and in CISA’s Known Exploited Vulnerabilities catalog.
→ Compliance security assessments
The Network Vulnerability Scanner can help you gather information and assess compliance with security standards. It makes auditing a much more effective task and supports security teams in maintaining compliance.
→ Security self-assessments
Conducting proactive network assessments is crucial to maintaining network security. To enhance the effectiveness of your network assessment process, evaluating and identifying the most critical aspects of your network infrastructure and giving priority to addressing those assets is key. This tool is ideal for conducting a comprehensive and thorough infrastructure test.
→ Third-party infrastructure audits
If you are an IT services or IT security company, you can use the resulting report to prove to clients that you implemented proper security measures in the infrastructure you are managing. This report includes the full list of network vulnerability tests the tool runs along with pre-filled remediation advice.
Architecture
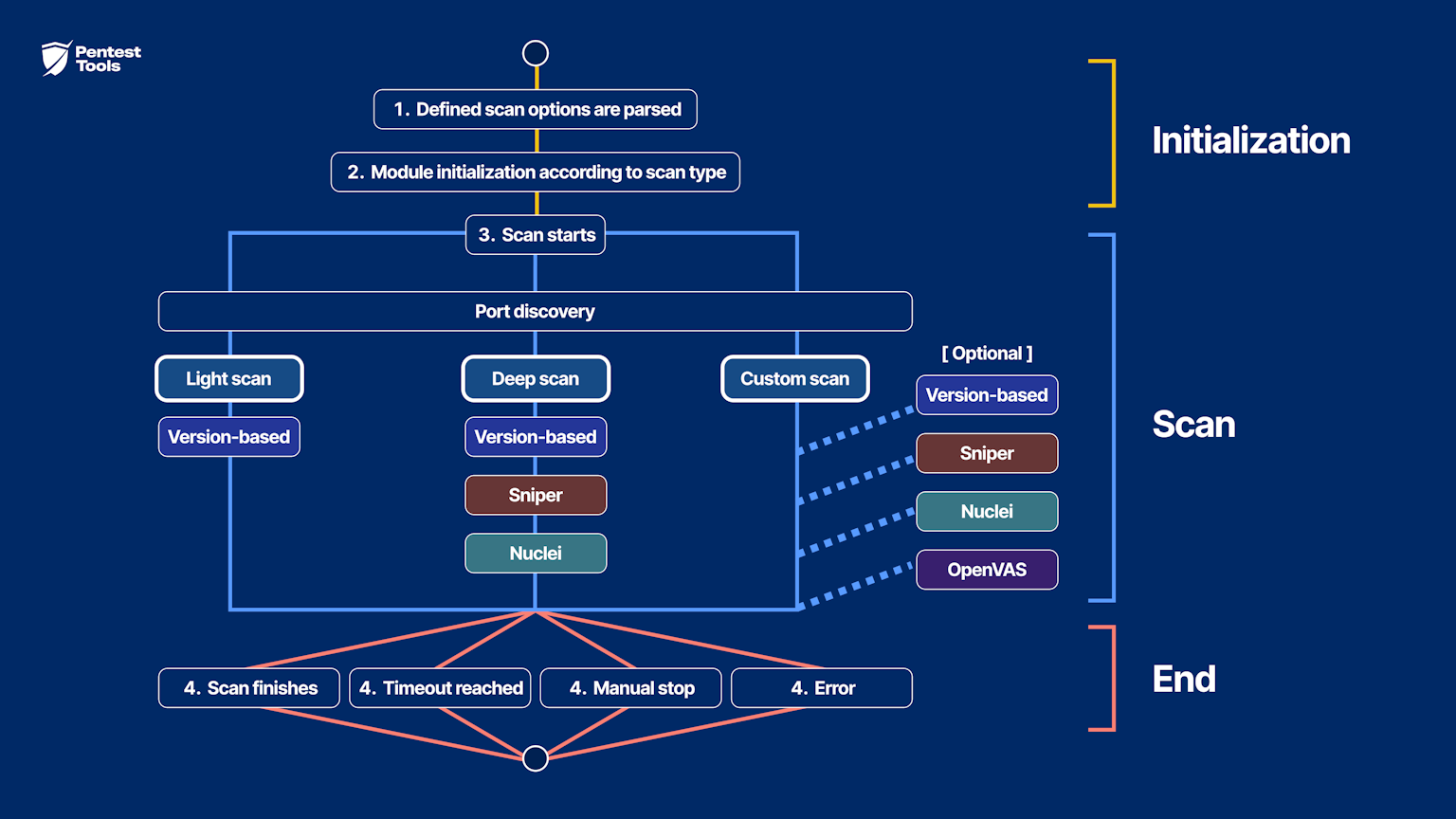
The Network Scanner’s architectural breakdown of the successive steps it takes when started can help you understand the way it works and configure it.
The scanning engine parses the scan options.
The scanning engines are initialized based on the selected scan type and added to the list of the tool's engines.
The scan process starts (during the scan process, the system calculates the minimum and maximum progress for each module):
↳ Host discovery: checks if the target is alive and executes port scanning; displays the Port Coverage finding containing a table with all discovered (open) ports.
↳ Version-based engine runs (for Light scan, Deep scan, and, if selected, in Custom scan).
↳ Sniper engine runs (for Deep scan and, if selected, in Custom scan).
↳ Nuclei engine runs (for Deep scan and, if selected, in Custom scan).
↳ OpenVAS engine runs (if selected in Custom scan).The Network Vulnerability Scanner runs until one of the following stopping conditions are met:
→ all the engines complete successfully
→ the user requests the scan to stop
→ the scan timeout period (default: 24 hours) is reached
→ an error occurs while performing the scan
Scanning engines
The Network Vulnerability Scanner uses four complementary scan engines. They can be used in conjunction (“Deep”) or selectively (“Custom”) as part of our predefined scan types.
Note: The scanner might fail to detect any open ports despite clear evidence to the contrary. This usually means that something (a firewall for example) is blocking the connection to the target. In this particular case, we advise conducting a subsequent scan with the "Check if host is alive before scanning" option disabled. Please see this detailed article for more guidance.
Version-based
The Light network scan type performs a very fast security assessment with minimum interaction with the target system. Based on the results returned by the port-scanning phase, it queries a vulnerability database to determine if the specific versions of the services are linked to any known vulnerabilities or issues.
This is the only engine the predefined Light scan option uses.
Sniper Auto-Exploiter
The Sniper Auto-Exploiter engine is a collection of custom vulnerability checks and modules that our team develops. These components serve as a proficient means of promptly and precisely identifying the majority of crucial vulnerabilities in renowned software applications.
A complete list of Sniper detection modules currently available in the Network Scanner can be found in our Vulnerability & Exploit Database.
Note: the Sniper Auto-Exploiter is also available as a standalone exploitation tool that you can run separately – and configure more granularly. See: Sniper - Automatic Exploiter.
Technical details
Sniper’s primary aim is bridging the disparity between the outcomes from common vulnerability scanners such as Nessus, Qualys, and OpenVAS, and the actual attack methods that genuine threat actors use. Traditional vulnerability scanners generate an extensive range of potential vulnerabilities, often flooding users with a significant amount of irrelevant information and false alarms. Conversely, real attackers tend to focus their efforts on a select few intrusion techniques that are exceptionally potent and precisely targeted.
While being a tool both capable of vulnerability detection and exploitation, the Sniper scan engine used by the Network Vulnerability Scanner only performs vulnerability detection. You can, however, use the findings generated by the Sniper engine in the Network Vulnerability Scanner, and exploit them with the standalone Sniper tool: Sniper - Automatic Exploiter (see the “Sniper integration” section below).
For a more in-depth technical overview of how Sniper works and a list of the modules it uses to exploit known critical vulnerabilities in high-profile software, please see its dedicated page.
OpenVAS
OpenVAS is a sophisticated vulnerability scanner and stands as an open-source solution capable of actively identifying numerous vulnerabilities across network services. Its comprehensive scanning capabilities extend to services such as SMTP, DNS, SSH, RDP, VNC, HTTP, and various others.
The OpenVAS methodology consists of establishing connections with each network service and dispatching specifically generated packets that require responses. Based on the nature of the response, it determines whether the service is vulnerable or not.
Note: as OpenVAS performs a considerable number of tests, the scan duration with this engine can vary significantly, ranging from 30 minutes to several hours. The duration primarily depends on the volume of open ports identified on the target host. The more open ports you scan, the more time-consuming the scanning process becomes because OpenVAS needs to execute a larger number of Network Vulnerability Tests.
Technical details
OpenVAS emerged as a forked alternative to the Nessus scanner in response to their transition to a commercial product in 2005. OpenVAS is currently under active development and maintenance by Greenbone Networks, with contributions and support from the wider community.
The core functionality of OpenVAS is implemented through individual tests, known as Network Vulnerability Tests (NVTs), which are encapsulated in plugins. These plugins are scripted using a language called NASL (Nessus Attack Scripting Language). OpenVAS boasts an extensive library of over 57,000 active plugins, enabling the detection of a wide range of vulnerabilities across various services and applications. This vast collection empowers OpenVAS to thoroughly assess potential security weaknesses in diverse network environments.
OpenVAS scanning policy
A variety of predefined policies are available for vulnerability scanning, but our scanner specifically uses the "Full and Fast" policy. This policy is designed to maximize efficiency by employing a significant portion of the available Network Vulnerability Tests (NVTs) and optimizing the scanning process by using information gathered from previous plugins.
For example, if a plugin identifies an FTP service running on port 2121, the "Full and Fast" policy triggers the execution of all FTP-related plugins specifically tailored to that port. Conversely, if no FTP service is detected, the corresponding plugins will not be executed, streamlining the scanning process and improving efficiency. This approach ensures that resources are allocated judiciously and avoids unnecessary scans for services that are not present, making the vulnerability assessment more effective.
Nuclei
An open-source project developed by ProjectDiscovery, Nuclei is primarily used for security testing and reconnaissance purposes. It can efficiently scan large numbers of network targets and web applications for common vulnerabilities, such as CVEs, cross-site scripting (XSS), SQL injection, server-side request forgery (SSRF), open redirect, and more.
Technical details
Nuclei makes it easy to send requests across multiple targets using customizable templates (Nuclei templates), ensuring accurate results with fewer false positives. It can quickly scan a vast number of hosts. It also supports scanning for diverse protocols, including TCP, DNS, HTTP, SSL, File, Whois, Websocket, Headless, and more.
Nuclei templates
Nuclei templates are predefined configurations or scripts that include specific security checks. These templates serve as a foundation for conducting security assessments using the Nuclei engine. Each template is designed to target a particular vulnerability or misconfiguration in web applications or network services.
Our Network Vulnerability Scanner uses network-related Nuclei templates that have the following tags: CVE, cnvd, DNS, network, SSL and WAF. In total, there are currently over 2100 network-related Nuclei templates configured in the Network Vulnerability Scanner. For a full list of them, please see here (part 1) and here (part 2).
Scan types
There are three predefined scan types: Light, Deep, and a Custom option that allows you to define the various scanner parameters such as the scanning engines used, ports, protocols, and so on.
Light
This option offers a quick and concise system overview. The speed of this scan mode comes from the Version-based engine it uses to identify vulnerabilities.
Configuration overview
Scanning engines used: Version-based
Ports scanned: Top 100 used by Nmap (click here for a full list of scanned ports)
Protocol type: TCP or UDP
Other scan options: Check if the host is alive before scanning (enabled by default)
Note: Despite its notable speed, this detection method is susceptible to generating false positives because it only relies on the reported service versions, which are subject to potential inaccuracies.
Deep
Thorough and complete network scanning. This scan type runs the Nmap port scanner on the top 5000 most common ports for TCP protocol or the top 1000 for the UDP protocol. It then runs three of the scan engines: Version-based, Sniper, and Nuclei.
Configuration overview
Scanning engines used: Version-based, Sniper, and Nuclei
Ports scanned:
TCP: Top 5000 used by Nmap (click here for a full list of scanned ports)
UDP: Top 1000 used by Nmap (click here for a full list of scanned ports)
Protocol type: TCP or UDP
Other scan options:
Check if the host is alive before scanning (enabled by default)
Enable Sniper extensive modules (disabled by default)
Custom
This scan type allows you to select the individual options of the network scanning flow (see the full parameter reference below).
Just like the other predefined scan types, it runs an Nmap scan on the designated ports. If no ports are explicitly selected, it will automatically scan the top 1000 most common ports and subsequently load and execute all the selected scanning engines, enabling a comprehensive and thorough scan.
Configuration overview
Scanning engines used: allows you to choose between Version-based, Sniper, OpenVAS, Nuclei, or any combination of these.
Ports scanned: allows you to define which ports to scan (predefined list, custom range, or custom list).
Protocol type: TCP or UDP.
Other scan options:
Check if the host is alive before scanning (enabled by default)
Enable Sniper extensive modules (disabled by default)
Parameter quick reference
Target | This specifies the target that will be scanned. It can be a single IP address or a hostname (ex: 8.8.8.8 or “ |
|---|---|
Scan type - Light | Quick scan type that provides a rapid network overview by using a custom-built vulnerability scanning engine that focuses on the top Nmap 100 most commonly used ports. |
Scan type - Deep | Uses predefined scanning engines (Version-based, Sniper, and Nuclei) on the top 5000 most common TCP ports or top 1000 most common UDP ports. |
Scan type - Custom | This selection allows for customization of the scanning engine and ports. At minimum, one scanning engine must be selected. If no specific ports or range are selected, the scanning process will default to the top 1000 most commonly TCP or UDP used ports. |
Scan type - Custom: Version-based | Option available only for the Custom scan type (this engine is automatically used during the Light and Deep scan types). Activate/deactivate the execution of the Version-based engine for your Custom scan. |
Scan type - Custom: Sniper | Option available only for the Custom scan type (this engine is automatically used during the Deep scan type). Activate/deactivate the execution of the Sniper engine for your Custom scan. |
Scan type - Custom: Nuclei | Option available only for the Custom scan type (this engine is automatically used during the Deep scan type). Activate/deactivate the execution of the Nuclei engine for your Custom scan. |
Scan type - Custom: OpenVAS | Option available only for the Custom scan type. Activate/deactivate the execution of the OpenVAS scan engine during your Custom scan. This engine is otherwise not used in the other scan types. |
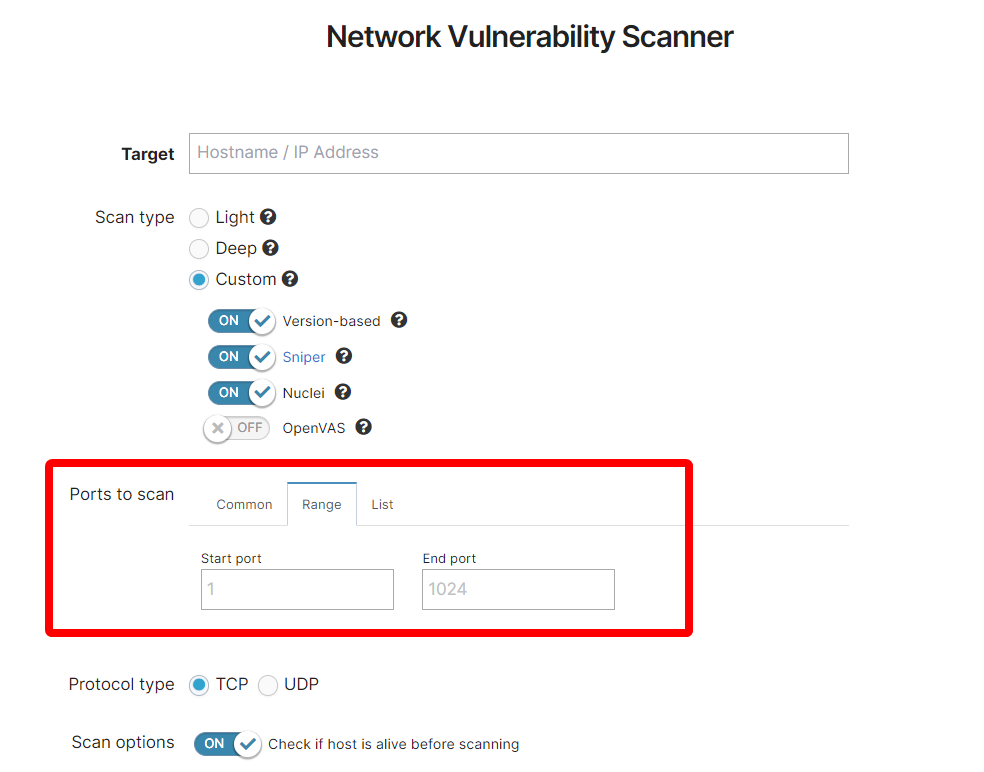
Ports to scan - Common | Option available only for the Custom scan type. Allows you to define which predefined port ranges you want to scan:
For the detailed port list corresponding to each of the options above, click here. |
Ports to scan - Range | Option available only for the Custom scan type.
|
Ports to scan - List | Option available only for the Custom scan type. Define an iterated list of the ports to scan, separated by a comma (“,”). |
Protocol type - TCP | Select this option to scan TCP ports. |
Protocol type - UDP | Select this option to scan UDP ports. |
Scan options - Check if host is alive before scanning | Check this option to enable host discovery. This will check if the target is alive before scanning it. See note above. |
Scan options - Enable Sniper extensive modules | Option available only for the Deep and Custom scan types, if the “Sniper” engine is specifically selected. Toggling this option allows the execution of Sniper modules that run for an extended period of time - including detection for CVE-2022-42889 (Apache Commons - Remote Code Execution) and CVE-2022-34265 (Django - SQL Injection). Note that activating this feature will increase the scan duration. |
Custom scan time | Define the maximum runtime allowed for the scanner (in minutes). The default is set to 1440 minutes (24 hours). A minimum runtime of 5 minutes can be configured when expedited results are desired. |
Notifications | Allows you to get notifications when scan results match the trigger conditions (see “ |
Schedule Scan | Define a time for your scan to run. This option is available when selected from the drop-down list next to the “Start Scan” (which is the default action set) button. |
Understanding the report
All findings detected by our vulnerability scanners undergo a classification process, with each of them being assigned a specific Risk Level. This categorization is determined by the severity level of each vulnerability, taking into account factors such as the Common Vulnerability Scoring System (CVSS) score (more information here) and our internal framework logic.
Risk levels
🟢 [Informational] - Findings that hold no inherent severity and can be addressed at your discretion. They can also be optionally excluded from the final report, based on your preferences.
🔵 [Low] (CVSS score <4) - Vulnerabilities classified as low-risk typically pose a minimal impact on the organization's business operations. These vulnerabilities usually increase the damage potential to a business when exploited alongside a high-risk vulnerability.
🟠 [Medium] (CVSS score >=4) - For successful exploitation, intruders need to actively manipulate individual targets when dealing with medium-risk vulnerabilities. While these vulnerabilities should not be disregarded, they demand a certain level of effort to be fully utilized in a real attack.
🔴 [High] (CVSS score >=7.5) - High-risk findings represent vulnerabilities that are susceptible to relatively straightforward exploitation by potential intruders. Exploiting high-risk vulnerabilities carries the potential for substantial downtime and/or significant data loss. It is crucial to prioritize addressing these vulnerabilities promptly.
Statuses
The “Status” column in the Findings section of the Pentest-Tools platform helps to monitor how effective remediation is or to selectively exclude specific findings from reports.
To modify the status of each of the findings, use the "Modify Finding" button located in the upper menu.
Open - This status denotes the default state assigned to newly identified findings by our scanning tools.
Fixed - Upon implementing remediation measures, findings can be modified to this status. However, if a previously fixed finding reappears in subsequent scans, it suggests potential inaccuracies in the applied remediation measures, which warrants a thorough verification.
Accepted - Findings can be designated as "Accepted" to indicate that certain issues will not be remediated. By marking vulnerabilities as accepted, they can be effortlessly excluded from reports with a single action.
Ignored - Findings labelled as "Ignored" are automatically omitted from reports. This preference is retained for subsequent scans performed on the same target.
False Positive - If there is reason to believe that a finding is wrongly reported, it could potentially be classified as a false positive. You have the option to navigate to designate a specific finding as either "False Positive". Just like for the “Ignored” status, this action ensures the automatic exclusion of the finding from the scan results.
Note: we strongly advise validating the findings (see below) in the report manually before marking them as “Ignored” or “False Positives”.
Validating findings
It is strongly advised to review all reported vulnerabilities and perform manual verification of each identified issue.
Note: The Sniper detection engine in the Network Vulnerability Scanner provides an automated validation procedure.
Exploiting findings: Sniper integration
You can use findings from the Network Vulnerability Scanner, generated by the Sniper detection engine, and employ the "Validate with Sniper" option to get proof of compromise.
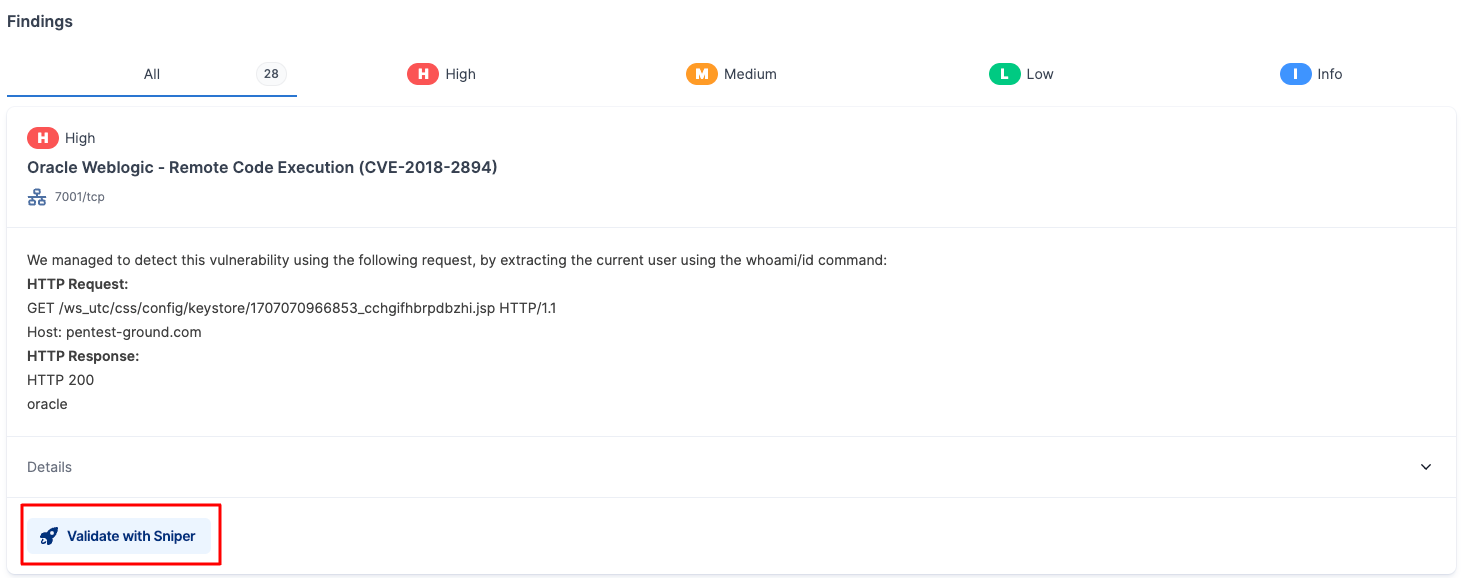
For instance, if the Network Vulnerability Scanner identifies a vulnerability in your application, such as the Proxyshell exploit chain, you can click the "Exploit with Sniper" button to access the Sniper – Automatic Exploiter tool and promptly verify if the vulnerability truly exists.
Simultaneously, this step gathers crucial information about your system through the list of artefacts that Sniper extracts.
Interface quick reference
The Network Vulnerability Scanner interface will undergo slight changes based on the type of scan you wish to perform (Light, Deep, or Custom), resulting in various options appearing or disappearing. Below, we provide a quick rundown of the UI's look and feel according to the selected scan type.
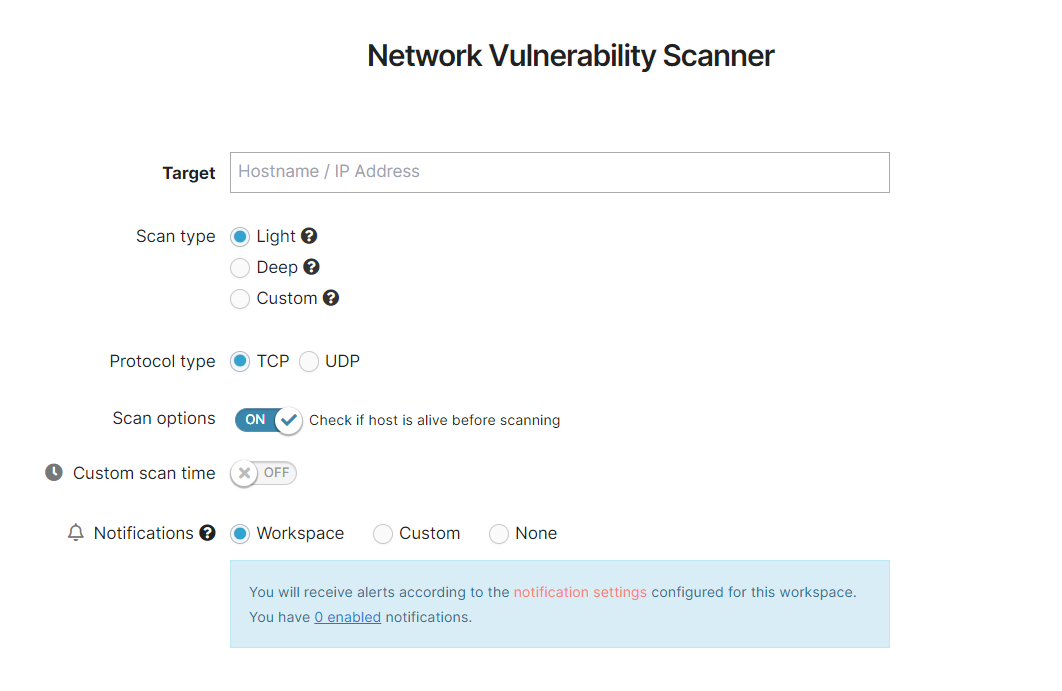
Light Scan
Only a few options are available; this scan type is designed to give you a quick overview of the network. You can choose the Protocol type (TCP or UDP), Check if the host is alive and define the scan notifications.
For a full rundown of the available options, please see the dedicated section, or this general support article: How to configure the Network Vulnerability Scanner.
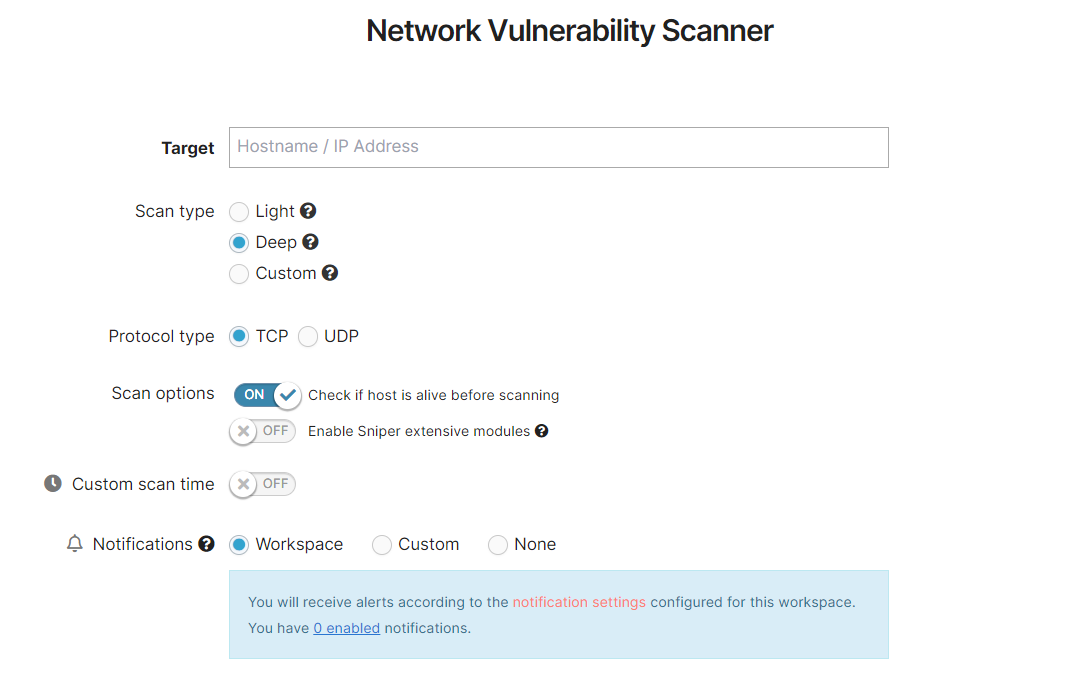
Deep Scan
Other than the options from the Light scan, more ports are scanned and you also can enable the Sniper extensive modules (disabled by default).
For a full rundown of the available options, please see the dedicated section, or this general support article: How to configure the Network Vulnerability Scanner.
Custom
This customizable scan type will give you access to all the options of the process, including the scan engines to be used (including the OpenVAS engine, which is only available through the Custom scan), and allow you to define specific ports or port ranges to be scanned.
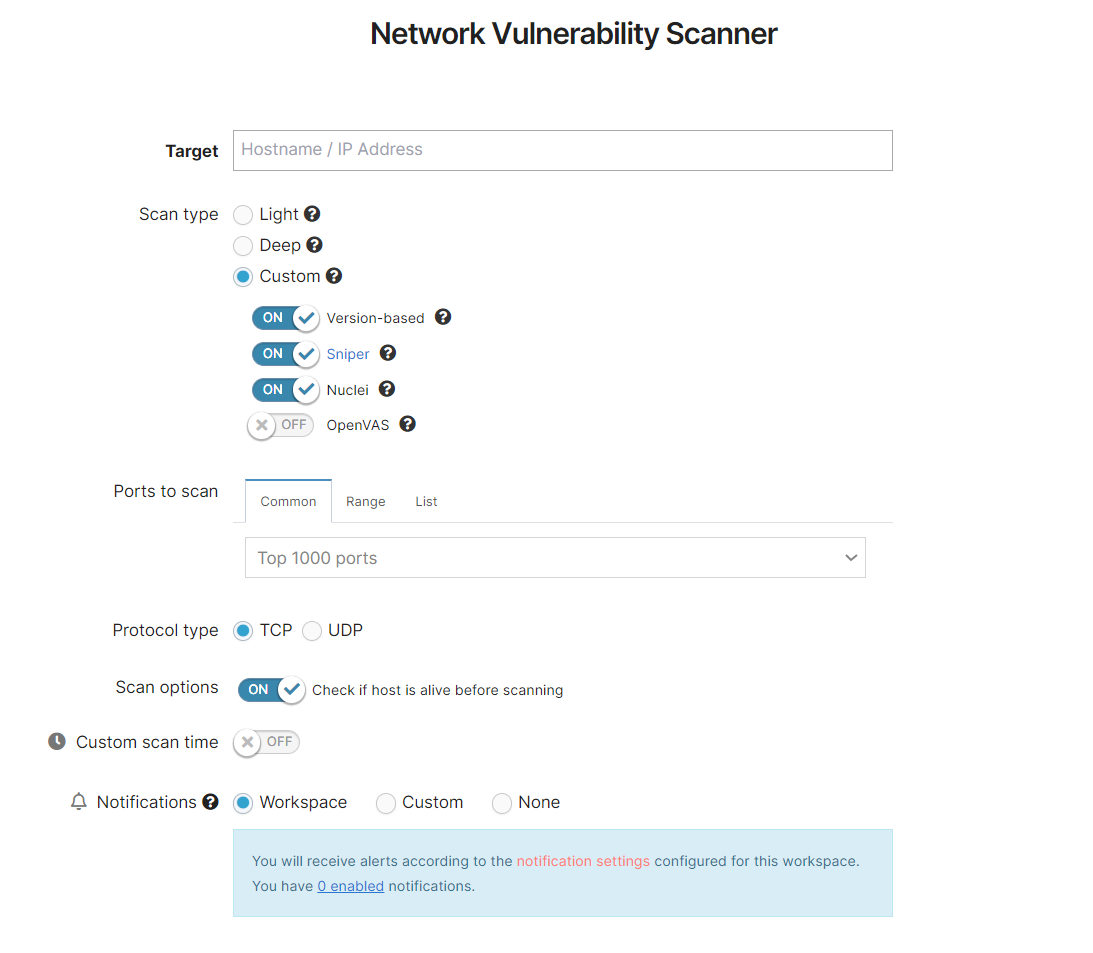
For a full rundown of the available options, please see the dedicated section, or this general support article: How to configure the Network Vulnerability Scanner.
FAQ’s
How to evaluate if my network is vulnerable?
From a deep scan and subsequent report, you can start to understand what your exposure is and which vulnerable endpoint malicious hackers might use to distribute malware such as ransomware or spyware.
If you need help with assessing your attack surface and the vulnerabilities and misconfigurations in your network devices, our certified team of penetration testing professionals can help.
How long will the scan take?
The duration of a scan can vary depending on the scanning engines being utilized, ranging from a few minutes to several hours. While it runs, it is possible for the scan to appear stagnant or unresponsive. To ascertain the current status, users can simply click on the target name, which will display a progress bar information tooltip, revealing the ongoing test being conducted.
It is important to note that the speed of the scan is influenced by factors such as the response time of the server and network latency on the server-side. Despite any delays encountered, the scan will ultimately reach completion.
If the scan appears to extend beyond the expected duration, it will reach our standard scan time limit of 24 hours and time out. In such cases, if a significant number of open ports are detected during the initial phase of the scan, we suggest dividing the scan into two parts, each focusing on a smaller port range.
Note: while long scan times are not uncommon (see above), if your scan process exceeds 24 hours, we recommend reaching out to our support team for assistance. This extended duration indicates a potential freezing or halted state of your scan.
Why does the TCP / UDP port scan appear stuck at 50%?
It is common for a particular step to require a longer duration to reach completion. It is strongly advised not to interrupt or halt the scanner, even if it appears to be stagnant or unresponsive.
If the scan appears to extend beyond the expected duration, it will reach our standard scan time limit of 24 hours and time out. In such cases, if a significant number of open ports are detected during the initial phase of the scan, we suggest dividing the scan into two parts, each focusing on a smaller port range.
Why am I receiving unexpected results such as false positives or false negatives?
While we make every effort to provide the most accurate results possible, automated scanning techniques may occasionally allow corner-case False Positives to slip through our validation systems or result in vulnerabilities going unnoticed. In such cases, we encourage you to actively report the issue to us for further investigation.
What OpenVAS scanning policy does the Network Vulnerability Scanner use?
While OpenVAS has multiple predefined policies, our scanner uses the one called Full and Fast. This policy includes most of the network vulnerability tests (NVTs) and is configured to dynamically chain these NVTs together instead of running them all randomly.
For instance, if a network vulnerability test detects the FTP service on port 2121, our Full and Fast configured OpenVAS will proceed to run all FTP-related NVTs on that specific port. However, it will not run these NVTs on other ports hosting services unrelated to FTP.
Is the Network Vulnerability Scanner on Pentest-Tools.com just a wrapper on top of OpenVAS and Nuclei?
No, it is much more than that. OpenVAS, although open-source, poses challenges during deployment and configuration. However, our implementation streamlines the process, enabling you to concentrate on scanning rather than dealing with deployment and maintenance. Pentest-Tools also consolidates the generated findings into a unified "Findings" report.
For Nuclei, we have made modifications to the description of network-related templates to ensure easy inclusion in scan reports. We actively focus on the "Evidence" section to accurately determine if a finding is a false-positive or not. Additionally, we continuously update the templates to achieve better detection rates.
For further information, FAQ’s and articles about how to use and run the Network Vulnerability Scanner, please check our Support platform.